THM – SSRF – Part 9
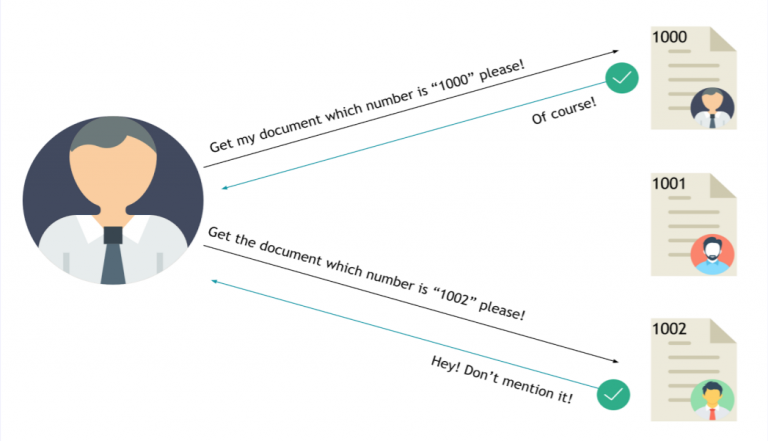
This is my notes from the Junior Pentesting course at TryHackMe. This course takes you through the basics and some advanced topics regarding penetration testing. What is an SSRF? SSRF stands for Server-Side Request Forgery. It’s a vulnerability that allows a malicious user to cause the webserver to make an additional or edited HTTP request…