THM – Command Injection – Part 11
Last Updated on January 25, 2022 by aghanim

This is my notes from the Junior Pentesting course at TryHackMe. This course takes you through the basics and some advanced topics regarding penetration testing.
Table Of Contents
What is Command Injection?
Command injection is the abuse of an application’s behaviour to execute commands on the operating system, using the same privileges that the application on a device is running with.
Command injection is also often known as “Remote Code Execution” (RCE) because of the ability to remotely execute code within an application. These vulnerabilities are often the most lucrative to an attacker because it means that the attacker can directly interact with the vulnerable system. For example, an attacker may read system or user files, data, and things of that nature.
For example, being able to abuse an application to perform the command whoami to list what user account the application is running will be an example of command injection.
Discovering Command Injection
This vulnerability exists because applications often use functions in programming languages such as PHP, Python and NodeJS to pass data to and to make system calls on the machine’s operating system.
In this code snippet, the application takes data that a user enters in an input field named $title to search a directory for a song title. Let’s break this down into a few simple steps.
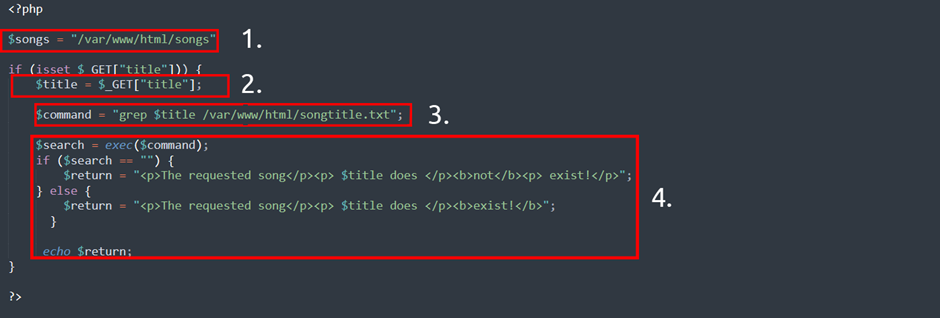
1. The application stores MP3 files in a directory contained on the operating system.
2. The user inputs the song title they wish to search for. The application stores this input into the $title variable.
3. The data within this $title variable is passed to the command grep to search a text file named songtitle.txt for the entry of whatever the user wishes to search for.
4. The output of this search of songtitle.txt will determine whether the application informs the user that the song exists or not.
Now, this sort of information would typically be stored in a database; however, this is just an example of where an application takes input from a user to interact with the application’s operating system.
An attacker could abuse this application by injecting their own commands for the application to execute. Rather than using grep to search for an entry in songtitle.txt, they could ask the application to read data from a more sensitive file.
This code snippet below is an application written in Python.
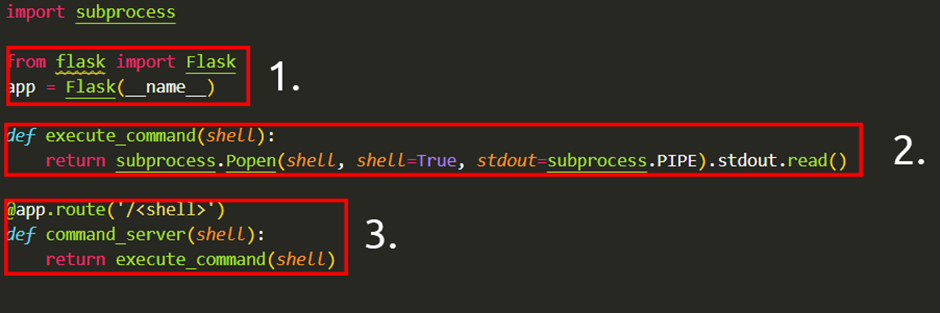
The “flask” package is used to set up a web server
A function that uses the “subprocess” package to execute a command on the device
We use a route in the webserver that will execute whatever is provided. For example, to execute whoami, we’d need to visit http://flaskapp.thm/whoami.
Exploiting Command Injection
Command Injection can be detected in mostly one of two ways:
- Blind command injection
- Verbose command injection
| Method | Description |
| Blind | This type of injection is where there is no direct output from the application when testing payloads. You will have to investigate the behaviours of the application to determine whether or not your payload was successful. |
| Verbose | This type of injection is where there is direct feedback from the application once you have tested a payload. For example, running the whoami command to see what user the application is running under. The web application will output the username on the page directly. |
Detecting Blind Command Injection
Blind command injection is when command injection occurs; however, there is no output visible, so it is not immediately noticeable.
For this type of command injection, we will need to use payloads that will cause some time delay. For example, the ping and sleep commands are significant payloads to test with.
Another method of detecting blind command injection is by forcing some output. This can be done by using redirection operators such as >
The curl command is a great way to test for command injection. This is because you are able to use curl to deliver data to and from an application in your payload. Take this code snippet below as an example, a simple curl payload to an application is possible for command injection.
curl http://vulnerable.app/process.php%3Fsearch%3DThe%20Beatles%3B%20whoami
Linux
| Payload | Description |
| whoami | See what user the application is running under. |
| ls | List the contents of the current directory. You may be able to find files such as configuration files, environment files (tokens and application keys), and many more valuable things. |
| ping | This command will invoke the application to hang. This will be useful in testing an application for blind command injection. |
| sleep | This is another useful payload in testing an application for blind command injection, where the machine does not have ping installed. |
| nc | Netcat can be used to spawn a reverse shell onto the vulnerable application. You can use this foothold to navigate around the target machine for other services, files, or potential means of escalating privileges. |
Windows
| Payload | Description |
| whoami | See what user the application is running under. |
| dir | List the contents of the current directory. You may be able to find files such as configuration files, environment files (tokens and application keys), and many more valuable things. |
| ping | This command will invoke the application to hang. This will be useful in testing an application for blind command injection. |
| timeout | This command will also invoke the application to hang. It is also useful for testing an application for blind command injection if the ping command is not installed. |
Remediating Command Injection
Vulnerable Functions
In PHP, many functions interact with the operating system to execute commands via shell; these include:
- Exec
- Passthru
- System
In the snippet below the application will only accept and process numbers that are inputted into the form. This means that any commands such as whoami will not be processed.
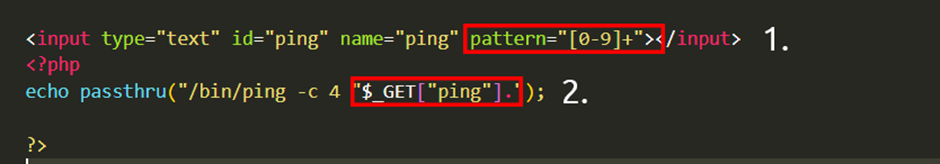
- The application will only accept a specific pattern of characters (the digits 0-9)
- The application will then only proceed to execute this data which is all numerical.
Input sanitisation
Sanitising any input from a user that an application uses is a great way to prevent command injection. This is a process of specifying the formats or types of data that a user can submit. For example, an input field that only accepts numerical data or removes any special characters such as > , & and /.
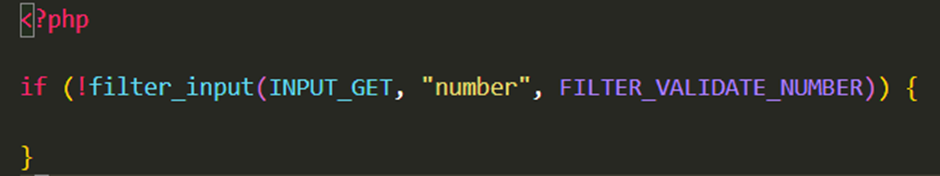
In the snippet below, the filter_input PHP function is used to check whether or not any data submitted via an input form is a number or not. If it is not a number, it must be invalid input.
Bypassing Filters
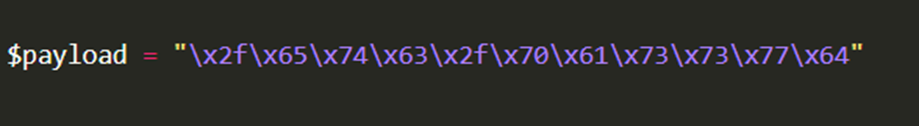
Applications will employ numerous techniques in filtering and sanitising data that is taken from a user’s input. These filters will restrict you to specific payloads; however, we can abuse the logic behind an application to bypass these filters. For example, an application may strip out quotation marks; we can instead use the hexadecimal value of this to achieve the same result.
When executed, although the data given will be in a different format than what is expected, it can still be interpreted and will have the same result.
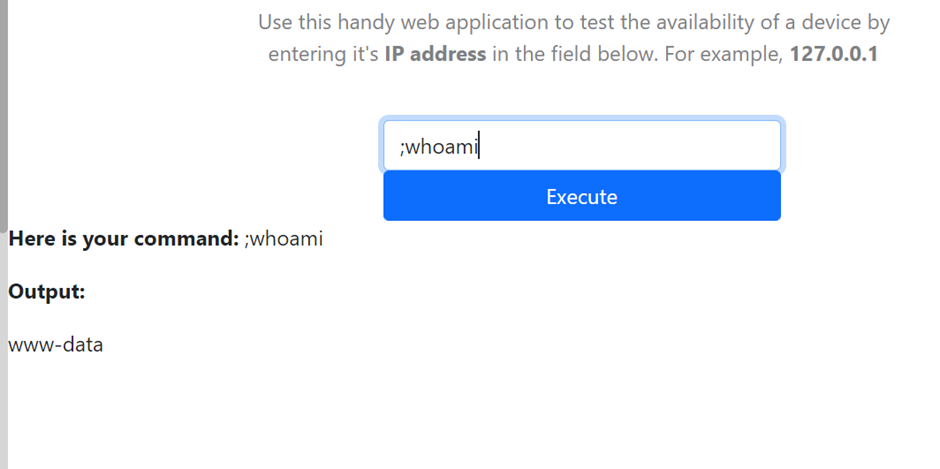
Practical: Command Injection
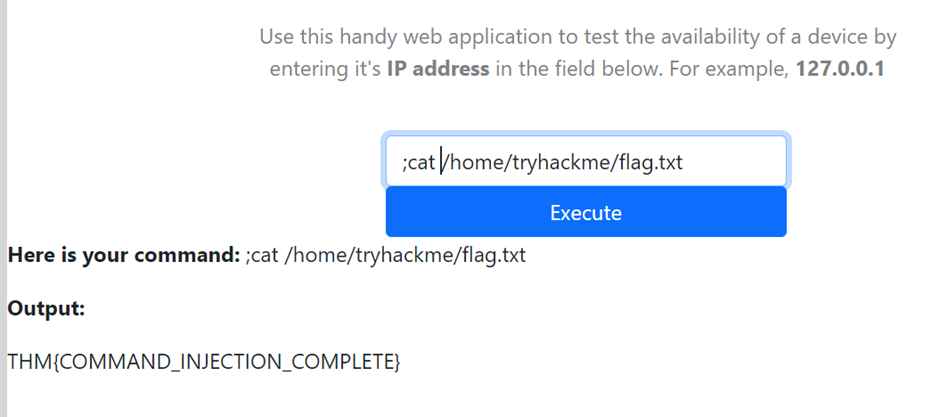
What user is this application running as?
What are the contents of the flag located in /home/tryhackme/flag.txt