TryHackMe – Network Fundementals – Part 1
Last Updated on January 25, 2022 by aghanim

Forewords
In this blog series I will write down my notes from the courses I take from TryHackMe. This series is from the Complete beginner course where I will go through Network security, Web App security, different tools I use etc.
I recommend anyone wanting to learn pentesting or defensive security to subscribe to TryHackMe. They have many rooms, from complete beginner to advanced.
Introduction Networking
The OSI Model: Overview
The OSI (Open System Interconnection) Model is a standardized model which we use to demonstrate the theory behind computer networking.
The OSI Model consists of 7 layers:
Application, Presentation, Session, Transport, Network, Data link, Physical
Layer 7 Application
Provides Networking options to programs running on a computer. It works exclusively with applications, providing an interface for them to use in order to transmit data. When data is given to the application layer, it is passed down into the presentation layer.
Layer 6 Presentation
Receives data from the application layer. This data tends to be in a format that application understands, but not in a standardized format that could be understood by the application layer in the receiving computer. Layer 6 translates the data into a standardised format, and also handles any encryption (the S in HTTP), compression or other transformation of the data. The data is passed to layer 5.
Layer 5 Session
Looks to see if it can set up a connection with the other computer across the network. If not, it sends back error and process goes no further. If a session can be established the its the job of the session layer to maintain it, as well as co-operate with the session layer of the remote computer in order to synchronise communications. Important because it creates a session that is unique to the communication in question. This is what allows you to make multiple requests to different endpoints simultaneously without all the data getting mixed up. (Opening two tabs in a web browser at the same time). When a session layer has successfully logged a connection between the host and remote computer the data is passed down to layer 4.
Layer 4 transport
The first purpose; choose the protocol over which the data is to be transmitted. Two most common is TCP (Transmission control protocol) and UDP (User datagram protocol). TCP is connection-based, which means the connection between the computers is established and maintained for the duration of the request. Allows reliable transmission as the connection can be used to ensure that the packets all get to the right place. TCP connection allow two computers to remain in constant communcation to ensure that the data is sent at an acceptable speed, and that any lost data is re-sent.
UDP is opposite. Packet of data is essentially thrown at the receiving computer. If it cant keep up then that its problem. (Video transmission like Teams can be pixaleted for example). TCP is choosen for situatuions where accuracy is favoured over speed (File transfers or loading webpage) and UDP would be used in situations where speed is more important (video streaming).
When protocol is selected, layer 4 divides the transmission up into bite-seized pieces (TCP called segments, UDP datagrams) which makes it easier to transmit the message successfully.
Layer 3 network
Responsible for locating the destination of your request. For example, the internet is a huge network, when you want tot request information from a webpage, its the network layer that takes the ip address for that page and figures out the best route to take. This is called logical addressing (IP Adresses), which are still software controlled. Used to provide order to networks, categorising them and allowing us to properly sort them. Most common form of logical addressing is IPV4 format.
Layer 2 data link
Focus on the physical addressing of the transmission. Receives packet from the network layer (inclueds ip address for the remote computer) and adds the phyiscal (MAC) address of the receeiving endpoint. Inside every network enabled computer is a network interface card (NIC) which comes with a unique MAC (Media acces control) adress to identify it.
MAC address are burnt into the card, that cant be changed, but can be spoofed. When info is sent across a network, its actually the physical address that is used to identify where exactly to send the information.
Layer 2 serves an important function when it receives data, as it checks the received information to make sure that is hasnt been corrupted during transmissions which could well happen when the data is transmitted by layer 1.
Layer 1 physical: Hardware of the computer. Electrical pulse that make up data transfer over a network that are sent and received. Convert the binary data of the transmission into signals and transmit them across the network as well as receiving incoming signals and convert them back into birary data.
| Questions | Answers |
| Which layer would choose to send data over TCP or UDP? | Layer 4 |
| Which layer checks received packets to make sure that they haven’t been corrupted? | Layer 2 |
| In which layer would data be formatted in preparation for transmission? | Layer 2 |
| Which layer transmits and receives data? | Layer 1 |
| Which layer encrypts, compresses or otherwise transforms the initial data to give it a standardised format? | Layer 6 |
| Which layer tracks communications between the host and receiving computers? | Layer 5 |
| Which layer accepts communication request from application? | Layer 7 |
| Which layer handles logical addressing? | Layer 3 |
| When sending data over TCP, what would you call the bite sized pieces over data? | Segments |
| Which layer would the FTP protocol communicate with? | Layer 7 |
| Which transport layer protocol would be best suited to transmit a live video? | UDP |
Encapsulation
As data is passed down eacher layer of the model, more info containing details specific of the layer in question is added to the start of the transmission. Example: Header added by the network layer would be source and destination ip addresses and header added by the transport layer would included (among other things) information specific to the protocol being used. Data link adds a piece on at the end of the transmission, which is used to verify that the data has not been corrupted on transmission. Added bonus of increased security, as the data cant be intercepted and tampered with without breaking the trailer. This process is called encapsulation. The process by which data can be sent from one computer to another.

When the message is receieved by the second computer, it reverse the process, starting at the phyiscal layer to application layer. Called de-encapsulation.
| Questions | Answers |
| What process would a computer perform on a received message? | De-encapsulation |
| Which is the only layer of the OSI model to add a trailer during encapsulation? | Data-link |
| Does encapluslation provide an extra layer of security? | Yes |
TCP/IP
Similar to OSI Model. Few years older and serves as the basis for real word networking.
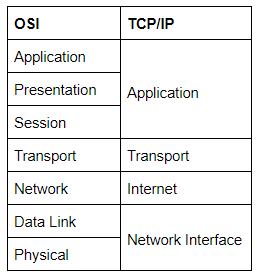
De-encapsulation and encapsulation work in exactly the same way with TCP/IP model as with OSI model.
TCP is a connection-based protocol. Before you send any data via TCP, must first form a stable connection between two computers. Process is called three-way handshake.
First computer sends a SYN packet (Synchronise) bit. Server respond with a packet SYN and acknowledgement ACK. Computer send a packet with ACK, confirming that the connection hs been setup successfully.

Ping
Ping command is used when you want to test whether a connection to a remote resource is possbile. Usually this will be a website on the internet, but could be for a computer on your home network if you want to check if config is correct. Ping works using ICMP protocol. ICMP works on the Network layer of the OSI model. Internet layer on the TCP/IP model.
Syntax for ping is
ping <target>Traceroute
Used to map the path your request takes as it heads to the target machine. Traceroute allows you to see each connection you go through. Allows you to see every intermediate step between your computer and the resource that you requested. Syntax “traceroute <destination>”. Windows utility “tracert”. Tracert utilises ICMP protocol, while the UNIX equivalent operates on UDP. Can be altered on both instances.
Whois
Whois allows you to query who a domain name is registered to. In Europe personal detailes are redacted, but elsewhere you can potentially get a great deal of information from whois search.
Dig and DNS
You make a request to a website. Computer first checks its local cache to see if its already got an IP address stored for the website. If not, next step. Will send a request to recurisve DNS server. Automatically known by the router. Usually, ISP maintain own recursive servers. If IP is not stored in cache, recursive server will pass the request to a root name server.
There are 13 root name DNS server in the world. The root name server keep track of the DNS servers in the next level down, choosing an appropriate one to redirect your request to. Lower level servers are called Top-level domain server.
Top level domain (TLD) servers are split into extensions. If you request .com, it will be handled by a TLD that handles .com domains.
As with root name servers, TLD servers keep track of the next level down: Authoritative name servers. When a TLD server receives your request for information, the server passes it fown to an appropriate Authoritative name server.
Authoritative name server are used to store DNS records for domains directly. Every domain in the world will have its DNS records stored on an authoritative name server. They are the source of the information.
Dig-command allows us to manually query recursive DNS servers of our choice for information about domains:
dig <domain> @<dns-server-ip>TTL of the record tells your computer when to stop considering the record as being valid – I.e when it should request the data again, rather than relying on the cached copy.
TTL is measured in SECONDS!





